|
Index of Materials re: Chelsea’s Resistance to Two Grand Jury Subpoenas |
Updated: January 2, 2020
January 2, 2020: Chelsea Manning Responds to United Nations Rapporteur’s Call For Her Release
Read the Letter from Chelsea Manning to Judge Anthony Trenga, where Chelsea explains the history of grand juries, after reflecting long and hard on the reasons for her resistance, at the request of Judge Anthony Trenga (original in PDF)
To keep up with developments, please follow the Chelsea Resists Twitter feed here. Donate to her Legal Fund here.
Updated Index:
- Past Written Statements by Chelsea’s Legal & Support Teams
- Timeline of Developments: Chelsea’s Resistence To A Grand Jury Subpoena
- Chelsea Resists Legal Defense Fund
- Chelsea Resists Twitter feed
- Address for writing Chelsea in Jail
- Dos and Don’ts for Writing Chelsea in Jail (IMPORTANT)
- Chelsea’s March 8th Statement
- Chelsea’s March 7th Statement
- RECAP PAGE FOR ALL LEGAL DOCUMENTS IN THIS CASE
- Solitary Confinement Statement by Chelsea’s Support Committee
- Daniel Ellsberg on Democracy Now: Chelsea Should Be Released
- Video of Chelsea Speaking outside the courtroom on March 8th – before her contempt hearing on Friday, March 8, 2019, when she was taken into Federal Custody.
- Daniel Ellsberg’s Statement of Support via the Freedom of the Press Foundation
- Daniel Ellsberg on Democracy Now (Video)
- Glenn Greenwald on Democracy Now (Video)
- References (Accurate Press Articles)
Solitary Confinement Statement From Chelsea’s Support Committee – March 23, 2019
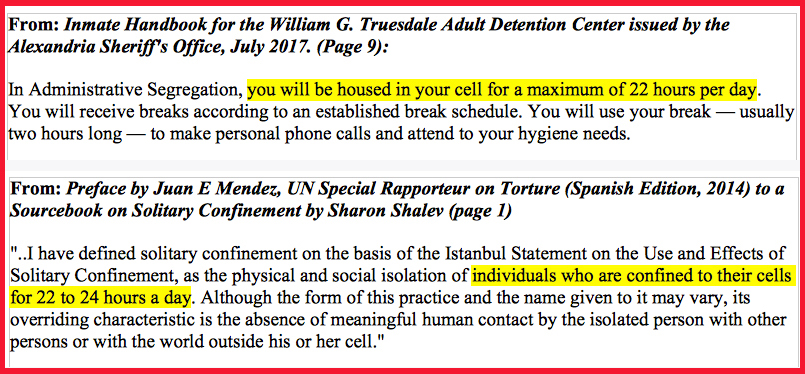
Chelsea is being held in solitary confinement. See the definition of solitary confinement compared to the jail’s own definition of the “Administrative Segregation” conditions under which Chelsea is being held:
Chelsea’s statement March 8th (from her Twitter account):
** Chelsea was taken into custody today for resisting a grand jury in the Eastern District of Virginia
Chelsea provided the following statement: pic.twitter.com/tWjEOFyhYn
— Chelsea E. Manning (@xychelsea) March 8, 2019
“I will not comply with this, or any other grand jury. Imprisoning me for my refusal to answer questions only subjects me to additional punishment for my repeatedly-stated ethical objections to the grand jury system.
The grand jury’s questions pertained to disclosures from nine years ago, and took place six years after and in-depth computer forensics case, in which I testified for almost a full day about these events. I stand by my previous public testimony.
I will not participate in a secret process that I morally object to, particularly one that has been historically used to entrap and persecute activists for protected political speech.”
Daniel Ellsberg’s Statement of Support
From the Freedom of the Press Foundation website:
“Chelsea Manning is again acting heroically in the name of press freedom, and it’s a travesty that she has been sent back to jail for refusing to testify to a grand jury. An investigation into WikiLeaks for publishing is a grave threat to all journalists’ rights, and Chelsea is doing us all a service for fighting it. She has already been tortured, spent years in jail, and has suffered more than enough. She should be released immediately.”
Chelsea’s Legal Defense Fund here:
Chelsea Resists Legal Defense Fund: https://actionnetwork.org/fundraising/chelsea-manning-needs-legal-funds-to-resist-a-grand-jury-subpoena
Address for writing Chelsea in Jail:
Chelsea Elizabeth Manning
A0181426
William G. Truesdale Adult Detention Center
2001 Mill Road
Alexandria, VA 22314
Dos and Don’ts for Writing Chelsea in Jail (IMPORTANT)
Statement from Chelsea Manning Regarding Grand Jury and Consequences Associated with Her Refusal – March 7, 2019:
Statement from Chelsea Manning Regarding Grand Jury and Consequences Associated with Her Refusal
“Yesterday, I appeared before a secret grand jury after being given immunity for my testimony. All of the substantive questions pertained to my disclosures of information to the public in 2010—answers I provided in extensive testimony, during my court-martial in 2013. I responded to each question with the following statement: ‘I object to the question and refuse to answer on the grounds that the question is in violation of my First, Fourth, and Sixth Amendment, and other statutory rights.’
“In solidarity with many activists facing the odds, I will stand by my principles. I will exhaust every legal remedy available. My legal team continues to challenge the secrecy of these proceedings, and I am prepared to face the consequences of my refusal.”
Past Statements by Chelsea & her legal and suport team:
- January 2, 2020: Chelsea Manning Responds to United Nations Rapporteur’s Call For Her Release
- August 7, 2019: Judge Says Chelsea Manning Can Pay Fines, Despite Evidence to the Contrary
- May 31, 2019: Chelsea Manning’s Legal Team Files Motion to Reconsider Sanctions
- May 23, 2019: Statement from Chelsea Manning and Her Lawyer Regarding Today’s Superseding Indictment
- May 16, 2019 (afternoon): Statement from Chelsea Manning’s Lawyers Regarding Chelsea Being Remanded Into Custody
- May 16, 2019 (morning): Statement from Chelsea Manning’s Legal Team Regarding Today’s Grand Jury Hearing
- May 10, 2019: Chelsea’s video statement
- May 10, 2019: Full Transcription of Chelsea’s video statement
-
May 9, 2019: Statements from Chelsea and her legal team: Chelsea Manning Released from Alexandria Detention Center After Grand Jury Lapses
- May 6, 2019 – Chelsea Manning and her Attorneys File Motion Declaring She will Never Cooperate with Grand Jury https://www.sparrowmedia.net/2019/05/chelsea-manning-and-attorneys-file-motion-declaring-she-will-never-be-convinced-to-cooperate-with-the-grand-jury/
- April 22, 2019 – Chelsea Manning and Her Attorneys Respond to 4th Circuit Court of Appeals Ruling Affirming Contempt and Continuing Her Detention https://www.sparrowmedia.net/2019/04/chelsea-manning-and-her-attorneys-respond-to-4th-circuit-court-of-appeals-ruling-affirming-contempt-and-continuing-her-detention/
- April 1, 2019 – Chelsea Manning’s Lawyers Ask Court to Release Her, Pending Appeal, Citing Abuse of District Court Discretion https://www.sparrowmedia.net/2019/04/chelsea-mannings-lawyers-ask-fourth-circuit-to-release-her-pending-appeal/
- March 29, 2019 – Lawyers for Chelsea Manning Ask Fourth Circuit Court of Appeals to Void Charges of Civil Contempt https://www.sparrowmedia.net/2019/03/chelsea-manning-grand-jury-appeal/
- March 23, 2019 – Lawyers and Supporters Condemn Chelsea Manning’s Ongoing Detention Under Solitary Confinement Conditions https://www.sparrowmedia.net/2019/03/lawyers-and-supporters-condemn-chelsea-mannings-ongoing-detention-under-solitary-confinement-conditions/
- March 8, 2019 – Chelsea Manning’s Support Committee: Manning’s Detention for Refusal to Provide Grand Jury Testimony is Pointless, Punitive, and Cruel http://www.balestramedia.com/chelsea-press-releases/2019/3/8/chelsea-mannings-support-committee-mannings-detention-for-refusal-to-provide-grand-jury-testimony-is-pointless-punitive-and-cruel
- March 6, 2019 – Statement from Chelsea Manning Regarding Grand Jury and Consequences Associated with Her Refusal https://www.sparrowmedia.net/2019/03/statement-from-chelsea-manning-regarding-grand-jury-and-consequences-associated-with-her-refusal/
- March 5, 2019 – Chelsea Manning Continues to Challenge Grand Jury Subpoena, Motion to Quash Denied, Remains Under Seal http://www.balestramedia.com/chelsea-press-releases/2019/3/8/chelsea-manning-continues-to-challenge-grand-jury-subpoena-motion-to-quash-denied-remains-under-seal
References: (work in progress – will keep adding to this)
1. Why Chelsea Manning Decided to Go to Jail in Protest, March 8, 2019, by Dell Cameron for Gizmodo https://gizmodo.com/why-chelsea-manning-decided-to-go-to-jail-in-protest-1833164311
“Manning, whose right to remain silent was supplanted as part of the grand jury process, was subpoenaed last month in the U.S. Justice Department’s not-so-sealed investigation into Julian Assange. Her defiance of this secret inquisition, however, is not about protecting the WikiLeaks founder at all.
Manning says she is resisting because she, like many other politically minded Americans, believes grand juries are an illegal instrument designed to aide prosecutors on fishing expeditions; a tool for stripping witnesses of their constitutional rights that has been historically used against peaceful political activists by men in power who would have them labelled “terrorists” and “enemies of the state…”
“Manning’s association with WikiLeaks nearly a decade ago was dissected in exhaustive detail during her 2013 court-martial, in which all manner of evidence about her brief contact with WikiLeaks, including the transcripts of their conversations, was presented. But now she is meant to regurgitate that story based on her own flawed memories while under the threat of prolonged incarceration if she finds any reason to refuse.
“We hope she changes her mind now,” the prosecutor, Tracy McCormick, told the Associated Press.
Although Manning is constitutionally protected from double jeopardy—from being charged twice for the same crime—her political right to silence has effectively been stripped away…”
2. Chelsea Manning Fights Subpoena — Showing How Federal Grand Juries Are Unaccountable Tools of Repression – By Natasha Lennard, March 2 2019 https://theintercept.com/2019/03/02/chelsea-manning-subpoena-grand-jury/
“Manning’s decision to fight her subpoena is an act of resistance against government repression and in defense of a free press.”
3. Chelsea Manning’s Lawyers Say No Formal Accusation She Gave False Statements During Court Martial (By Dell Cameron For Gizmodo)
4. Court Unseals Documents Regarding Chelsea Manning Subpoena (Documents are available via Lawfareblog)
5. The 4th Circuit Court of Appeals denied Chelsea’s Appeal & Bail Motion last Monday, April 22. Here are statements from Chelsea and her team: https://www.sparrowmedia.net/2019/04/chelsea-manning-and-her-attorneys-respond-to-4th-circuit-court-of-appeals-ruling-affirming-contempt-and-continuing-her-detention/
6. Chelsea has been let out of her solitary confinement conditions (Administrative Segregation), the definition of which, is nearly identical to the UN Special Rapporteur on torture’s definition of solitary confinement.