You can download video (MP4) to the John Perry Barlow Symposium here at the Internet Archive – it is released under a Creative Commons Public Domain License. Transcription by Lisa Rein with a little help from Teme. (Still took many hours of fixing up and matching timecodes – Journalists! I tried to make it easy for you to edit clips as needed :-)
Timecodes work for the downloaded mp4 OR the Youtube video. For the codes to work properly in both places, the music was left at the front of the video (when it was uploaded to the Internet Archive).
Cindy Cohn: Hello everyone. I just wanted to give everybody a five minute warning. We’re going to start in five minutes. We decided to delay because my co-emcee Cory Doctorow got delayed by the weather and we’re hoping he can make it here. And there’s a long line out front. So, five minutes!
I do think it’s somewhat appropriate that we’re starting late because it was notorious at the EFF board meetings that Barlow always arrived late – and he always had a really good story. So there’s space for people coming in, if you’re not next your neighbor go ahead and slide over – and ask them how they know Barlow, because chances are there’s a very good story there… [00:48:21]
Brewster Kahle: Welcome to the Internet Archive. And welcome to the John Perry Barlow symposium. Welcome. I’m Brewster Kahle, founder of the Internet Archive and welcome to our home. How many of you have not been here before? Ah! Welcome to the Internet Archive. And just sort of “where are you?” You’re in a former church. A Christian Science church. We thought we’d flatten the floors and make it into a library. But then we saw these great pews and we thought oh I could put up with all the awesome pews.
So thank you very much for coming. And just a few things to sort of look at that are kind of fun, If you crane your head, those servers in the back actually are 10 petabytes or about one quarter of the total primary copy of the Internet Archive and they’re live; they are being served to everybody in the world. Every time a light blinks is somebody uploading something or downloading something from the archive. And also just the little statues that are around the side. They’re us. If you work at the archive for three years, then we make a little statue and celebrate the people that are working on the civic side of the Internet Archive. [00:49:52]
And I’m very glad that you could come for the John Perry Barlow symposium. Close friend, board member, co-board member with the Internet Archive, with myself, on the EFF. And he was the first recipient of the Internet Archive Hero Award. And the reason why was because of his concept of sharing. And so he’s meant something I think to a lot of us. And I think of technologies, when they are new and we show them to people. It’s kind of a Rorschach test. If you ask people what is this new technology say “the Internet.” You learn more about the observer than the observed. You learn about how people see their world. And John Perry Barlow came at it as “radical sharing” and I think that embodies my internet. That that is the way I sort of think of and was inspired by this. So I think it’s a good match to have this event here at the Internet Archive. No further ado. There will be a whole sequences of speakers and thank you very much for coming. [00:51:04]
Cindy Cohn: Afternoon everyone. My name is Cindy Cohn and I am proudly the Executive Director of the Electronic Frontier Foundation. As I mentioned some of you might not have been in the room. Cory Doctorow has been held up by San Francisco International Airport’s unwillingness to deal with rain. And he’s he’s on his way here and we hope to have him soon. But so I’m going to do the best I can and I will not even attempt a Cory Doctorow interpretation, but I do want to extend our initial thanks to the Internet Archive for making this happen. We love you guys. This went from idea to execution so fast. I want to thank John Perry Barlow’s daughters for working with us on making this so easy. You’ll hear from two of them today. As a friend of Barlow for a long time, I really want to extend take a moment to extend a thanks to Alden Bevington and Jerilyn Lee Brandelius for the work and the help that they gave to Barlow during his last years. We should all have such good friends.
I want to thank the speakers for jumping, when I asked if they would come speak and throwing this together a little bit by the seat of our pants. I hope you’ll all bear with us. But I think the seat of our pants is in honor of Barlow’s spirit anyway, so I feel good about that. I want to thank all of you who donated to EFF and the Freedom of the Press Foundation outside. We do good work because we stand on the shoulders of giants and you guys are the giants. I want to welcome all the people who are watching over streaming or all of you who took advantage of your copyright fair use right to time shift this and are watching it at a later date. We appreciate it. I do want to note that there are some documentary filmmakers here who are going to be interviewing people and taking some crowd shots. If you want to be in them you’re welcome to be in them. If you don’t, you might want to steer around them. We don’t want anybody to have their face public and it doesn’t want to have their face public here today.
This is a bittersweet event for all of us who are here today. Every single person in this room wishes that Barlow was here with us, instead of us still celebrating his legacy. It’s bringing things back up for a lot of people, me included, about what horrible loss we’ve all suffered as a community. But here we are today, and our goal is to honor his legacy. And what a legacy it is. Originally we wanted to have this event address all of Barlow’s ideas across his entire life ranging from his anti Vietnam work to his anti-nuclear work to his poetic song lyrics that stick in your head over and over again to his environmental work to maybe even something about ranching in Wyoming.
But honestly it was just too much. We knew that he wouldn’t want us to just skirt the surface of his life but instead go deep. And so I picked the topic that is the one that speaks most to me and to all the rest of the city. Which is his legacy of Internet and Internet freedom. [00:54:29]
I’m delighted at all the people who came forward to do this with us today. So a little about our format. A little about our format. What I’ve asked each of our speakers to do is to select a quote from Barlow that inspired them or that they think is important about Internet freedom and give about eight to 10 minute presentation around it. We’ll have a Q and A after the first four speakers and another Q and A after the second four speakers. There are index cards in the pews in front of you, if you have a question that you want to put in the Q and A please go ahead and write it on it and we’ll have volunteers who’ll walk the aisles and pick them up. Cory when he gets here and I will be gathering them and presenting them during the Q & A But to start. We’ve asked Anna Barlow if she would come up and say a few words about her dad. [00:55:52]
Anna Barlow: Welcome everyone. Well I just want to say this is such a wonderful event for my family and I. And on the way over here I was thinking what a great thing it is that my dad doesn’t have to be bummed about missing parties anymore because now he can kind of go to all the parties, and he gets the best seat in the House which is which is great. So he would be so tickled about this amazing collection of some of his truly favorite minds and thinkers of all time in one room talking about the ideas that he was most inspired by. Most of them happen to be good friends but that’s just kind of how he rolled; with people that intrigued him the most. This speech was thrown together in the past few days so bear with me here. But it’s an honor to share some thoughts about him here.
The fact that it’s in conjunction with honoring him and his work – which has always been one of his favorite things – is a real treat for him to say the least. And I feel very much that he’s with us today and this weekend. And it’s I’m sure he’s giddy for this beautiful gathering. So thank you all so much for being here. And to EFf and the Internet Archive archive. My dad was kind of like a roving psychedelic data collector slash cowboy spy. The majority of his life.
And I remember as a little girl him coming home to rural Wyoming from his travels. Being so fascinated by these trinkets and books and artifacts from the far reaches of the world. We got to join him on many of these adventures as well as spend some time with him in his home in New York and San Francisco. But for the most part he seemed to always be in a different country every time I spoke with him, most of my life. And I remember him explaining to me as a little girl it wasn’t so much the things in these places that made them so special to visit, but it was really the people that lit up and fueled his love for exploration. When he got sick in the past few years I realized that although this physical presence was stationary, his adventures didn’t stop they just started coming to him. For the first time in his life, my dad was in the same place multiple months at a time, which meant that the people that loved him from all over the world actually knew where to find him.
So they started to come to visit him. Some regularly from across town. Others flew from across the globe just for a day. But everyone that came. No matter how close they were or how well they knew each other came for the same reasons. Beyond just loving him, they came to feel inspired. To feel understood. They needed to have their brains just completely turned inside out and handed back to them in 15 minutes which was really good at. Or sometimes most dependently they needed to just have a good laugh, which he was sure to supply. Even in his darkest of days whether he was meaning to or not, the man could get a laugh out of an old family dog. In fact he often said “it’s humor that saves us from despair.” And up until the very last day, he was still cracking jokes that ended in uncomfortable laughter, uncontrollable laughter (sometimes uncomfortable haha). [00:59:09]
Over the course of the past few years, I found myself returning time and again to the station here in San Francisco to be with him. To help how I could. But I also came for that inspiration and that wisdom and that laughter. I met some incredible visitors of his, over the past few years. Physicists who taught alongside at Harvard. Brazilian supermodels who are still in love with him from 10 years ago at Carnival. Famous suit makers. His old pal, Joey Scalone, that made his favorite deli sandwich in New York, with extra Miracle Whip, that they had just there for him. Dancers. Writers. Politicians. Magicians. Janitors from old hospitals. Leaders of biker gangs. Healers. Priests and childhood friends. Each with a different special story of what my dad meant to them. Each with a different lens of the strong love they felt for him. I remember each distinctly, as they were unique.
One of my favorite visitors really helped me understand my fathers impact on the world of the Internet in a way that I hadn’t before. And, to this day, was one of my favorite Barlow interactions. One day, as my dad was in the hospital, and I was, for whatever reason, feeling a little short wired and tired. Two men walked in with baggy clothes and neck tattoos, and I thought “where in the world does this puzzle piece fall on the insane mosaic of my dad’s life?” My dad was sleeping and the nurse asked for us to go in the waiting room. At first I didn’t feel very talkative, but from pure curiosity, I asked how they knew my dad. [01:00:52]
“He saved our lives. One of them said completely candidly. The other nodded.
“Oh yeah? How’s that?” I asked.
They went on to explain in such a poignant beautiful way, that my dad to them was a contemporary noble knight that rode on and rode in on his white stallion, and one of the most dire moments in their lives and swept them out of harm’s way and they owed everything to him.
These guys, I came to find out where a couple of the first original “hackers” The original whistleblowers who cracked the code to access databases for the good of humanity who fought for the truth. They had been thrown into jail for accessing information that should be shared for the public’s well-being and they were looking at extensive prison terms and my dad fought day and night to get them out. He didn’t know them well at this point, but he felt it was important to stand up for what they were doing, but more importantly to stand up for the people’s right to know the truth. (Cheers and applause from Audience.) [01:01:50]
To have access to that truth; to protect the availability that the Internet offered in a way that was more raw and accessible to information than ever before. He knew that this was an imperative thing to fight for, and it was second nature for him to fight as hard as he could.
Those men those men now live in Silicon Valley with successful startups and families. I wish I remember their names; they might be here. But it was a great interaction and it resembles such a small drop in the bucket of impacts that my father has had in his pursuit for protecting free speech. The right to access it and the pioneering of the Internet as we know it. So thank you dad for all of those important things of vital importance now more than ever to my generation, as well as to every generation to come.
If there’s one thing that my dad believed in more than anything, it was that everyone and everything is connected. The fabric of our lives is a never ending network is a never ending network of connectivity, and the internet nerd network mirrors that in a way that fascinated him entirely until his very last day. He said recently in reference to the internet. “I mean think of how expansive it is. It’s just an extensive ecosystem. It’s capable of keeping God company.” Followed by one of his whimsical chuckles. We’re so thrilled to celebrate him today and all of his work in pioneering free speech and just all of the impacts that he had to keep us in line with what’s important about honoring knowledge and truth today.
So thank you so much for being here. Big things to the EFF and the Internet Archive and we look forward to the speakers. [01:03:36]
Cindy Cohn: (There’s a microphone pop and Cindy says “OMG everyone I’m so sorry.”)
All right. Thanks everyone. I’d like to call the first panel up. Our first panel of speakers is Mitch Kapor founder of EFF along with Barlow (&John Gilmore:), Pam Samuelson, Trevor Timm. And and we’ll have a fourth speaker who’s going to have to come from a faraway place. If you guys would come up please.
While they’re getting settled, I want to take a minute and frame some things a little bit. To me, what Barlow did for the Internet was to articulate more, and more beautifully than almost anyone, that this new network had the possibility of connecting us all. He saw that the Internet would not be just a geeky hobby or a toy or only a place of the military or of the academics, which is what a lot of people at that time believed, starting with the Deadheads like me, who used it to gather an otherwise nomadic tribe, he saw it as a new lifeblood for all humans who longed for connection, but had been separated. He talked about this in the context of Pierre Teilhard de Chardin, an evolutionary scientist and paleontologist. Barlow said that Teilhard had a vision of evolution which indicated to him that the evolutionary process was about to leave the carbon basis in a sense, and become an evolution of the mind. That’s what we were creating on the planet; the collective organism of consciousness. That’s the process that is taking place and what Teilhard called the “Noosphere.” It’s the next layer of evolutionary process; the layer of mind and thought.
So, Barlow saw the Internet as a chance for all of us to kind of start over with a clean slate and use this moment of evolution to build the layer of the mind and through that build the kind of world we wanted to live in, as opposed to the one that we had all inherited that it well and the mindset of the 1960s, where in the midst of a terrible strife and death and war, a set of people including Barlow, were actively searching for a better way. [01:06:12]
But Barlow also recognized this new world of connection was one that we could use for good, or for ill, and that it was going to be up to us which one we did. And he famously put down his marker on the side of good. Another thing Barlow saw was that the movement into the digital world was going to be inevitable. He saw that the early Internet was designed and used mainly by what he called “white males under 50, with plenty of computer terminal time, great typing skills, high math SAT’s, strongly held opinions on just about everything, and an excruciating face to face shyness especially with the opposite sex.” I believe there are some of those here today. In an essay in the new reader called “Is there there, there in cyberspace?” He recognized all of this and the limitations that it created. Yet still, he put his marker down on hope: “When we are all together in cyberspace then we will see what the human spirit and the basic desire to connect can create there. I am convinced that the result will be more benign if we go there open minded, open hearted, and excited with the adventure, than if we are all dragged into exile.” [01:07:34]
Despite its current and perhaps in some areas permanent insufficiencies, we should go to cyberspace with hope, because groundless hope, like unconditional love, maybe the only kind that counts. Barlow and I didn’t always agree on everything, especially about how to bring about this future world, but we both believe that this was a fight worth having, and that to me is his strongest legacy.
So let’s start with our esteemed panel. I’m going to I was going to introduce you all, but I’m really going to try to wait for Cory for this because he had such great introductions and I cannot do them. But let me start with Mitch Kapor. He’s a pioneer of the tech industry and a longtime startup investor. He founded Lotus Development Corporation and designed Lotus 1 2 3. The first killer app which made the personal computers ubiquitous in business. He’s the co-founder with Barlow and John Gilmore of the Electronic Frontier Foundation. He was the founding chair of Mozilla, creator of the Firefox web browser, and currently he works to bring together the worlds of business and social impact and to diversify the tech ecosystem.
One of the things that Mitch gave us, that we still use all the time at the Electronic Frontier Foundation, is the idea that architecture is politics. That the idea of embedding cooperation, mutual aid and the sense of civic duty into the Internet’s protocols and operations makes our world better, and that we need to continue to push for that.
So now, without further ado, Mitch Kapor.
Mitch Kapor: Thank you Cindy, and hello to everyone. So many old friends and familiar faces here today. I thought I would read just five short sentences from EFF’s first public statement. “Across the electronic frontier.” It bears both of our names as authors but as you’ll hear it’s really in John’s voice and it sets the tone for what was to come. [01:10:00]
(He starts reading: “Over the last 50 years the people of the developed world have begun to cross into a landscape unlike any which humanity has experienced before. Cyberspace, the repository for all digital or electronically transferred information, will be the venue for most of what is now commerce, industry, and broad scale human interaction. It is the homeland of the information age. The place where the future is destined to dwell. Certainly the old concepts of property, expression, identity, movement, and context, based as they are on physical manifestation, do not apply succinctly in a world where there can be none. Sovereignty over this new world is also not well-defined. It is therefore a perfect breeding ground for both outlaws and vigilantes.” [01:10:58]
So first of all, this was in 1990. If you can think back, or look back if you’re not old enough to have been there, just prehistoric times. Five years before the web as we know it was even born. Almost no one was on the Internet. It was still very much a research and military driven network that was just beginning to be made available to the public. But Barlow absolutely nailed its essential character and what was going to happen. And that was his genius. And that expression of it was quintessentially Barlovian and it was visionary and poetic. But what he said had enormous practical consequences. And my role in this; I did a bunch of things. I brought some money. I brought some entrepreneurial energy. But as John liked to say I always came equipped to provide Barlow with a hyperbolectomy.
But at the same time, you should know, that so many of the stories that he told were literally true, not literarily true. So, for instance, as he wrote in Crime and Puzzlement. I really did detour my jet to Pinedale, Wyoming. I was on a trip from Boston (where I lived at the time in Silicon Valley) and I could not stop thinking about the dangerous ignorance of the law enforcement’s vendetta against teenage cyberspace vandals and I needed to talk to the only other person I knew who really got it and that was John Perry Barlow. And I flew the jet and stopped in Pinedale, and we connected, and you know the connection was one, a bit the way alien abductees sharing their UFO experiences have. They’re just trying to make sense of this weird thing that’s happened to them, and how to tell it to the larger world. (And that was his metaphor by the way.) [01:13:27]
And thus was born a partnership and like a rock band, unsurprisingly we took our show on the road, not to the Fillmore, but to hearing rooms in the Senate and the house, and inside the bowels of the CIA (where we smuggled in listening devices), into the heart of Silicon Valley, into more than a few dark basements of teenage hackers, and more than one courtroom.
Yes, the EFF got its start as a civil liberties organization, and for decades, I resented the way The Wall Street Journal characterized us as a “hacker defense fund,” but you know that’s not completely unfair. The issue was it wasn’t just that. Civil liberties were a place where Barlow and I came together, despite our very different politics. But the legacy of EFF, and what we created and what he brought to it, was far more than that.
In hindsight, the biggest impact that I think we had, was in raising consciousness. That these issues matter: property, expression, identity, and movement, and that things were changing, and they were going to change a lot and soon. And there was an urgency to get ahead of the issues before the issues got ahead of us. And to do it in a way that was as thoughtful and as generous of spirit as possible. [01:15:12]
And one of the moments of which he and I were both justifiably proud, was when, the first time, we saw in one room, the hackers and the feds shaking hands and seeing each other as human beings and not faceless enemies. Well, it’s nearly 30 years later now. If anything, I think we underestimated the transformative impact of information technology. And while the crises of today are deeply, deeply troubling, I believe we’re all better off for having gotten an early start; even if, as is surely the case least, if you ask me, we got some of it right and a lot of it wrong. But Barlow never gave up hope and neither should we. And I can feel his generous and optimistic spirit right here in the room today inspiring all of us. Thank you. [01:16:30]
Cindy Cohn: Our next speaker is EFF current board member Pam Samuelson. Pam is the Richard M. Sherman Distinguished Professor of Law at the Berkeley Law School and co-director of the Berkeley Center for Law and Technology. She’s been a member of the Board of Directors of EFF since 2000, and is proud to have succeeded John Perry Barlow as the Vice Chair of that Board. Although Barlow did make us give him another role which was the Rockin Vice Chair. I think it’s the Rocking Chair. Yeah, sorry about that.
She is also co-founder and chair of the Board of the Authors Alliance, a Non-profit Organization that represents the interests of authors like Barlow who want their work to be more widely available and who want to take advantage of opportunities to share their work in digital networked environments. Her most Barlowesque writing was “The Copyright Grab,” published by Wired, in January 1996. Now I’m going to try to riff Cory a little bit. Cory wanted to point out that the Internet has these natural pairings between kind of what Cory called “loony-ass visionary types” and serious, incredibly well-informed, sober, razor sharp adult supervision. (Often, women.) [01:18:12]
And I certainly inherited your role (looking over at Mitch Kapor) as the hyperbolectomy person for John Perry and as Cory points out those pairings are frequently devastating to our audience. You line them up Barlow and we’ll knock them down with the logic. I think the original one of these pairings was Pam Samuelson and John Perry Barlow on the question of copyright and the Internet. Pam?
Pam Samuelson: So, as requested. I will start with a quote that I really like from John Perry Barlow. “Think of the net as an ecosystem. It is a great rain forest of lifeforms. Ideas, which like organisms, these patterns of cells for reproducing, evolving, adaptive information that express themselves, and schemes of carbon, require other organized organisms to exist. Imagine the challenge of trying to write a song if you’ve never heard one. As in biology. what has lived before becomes the compost for what will live next. Moreover, when you borrow or for that matter, “steal” an idea that first took form in my head, it remains where it grew, and you, in no way, lessen its value by sharing it. On the contrary, my idea becomes more valuable, since in the informational space between your interpretation of it and mine, new species can grow. The more such spaces exists, the more fertile is the larger ecology of mind. [01:19:47]
So, Barlow’s major contribution in the field of copyright. And, he really did. Was “The Economy of Ideas” article that was published in 1994 in Wired magazine. And honestly, it’s been cited 742 times in the law review literature. Which, I’m telling you; there are people in my field who would just die to get that many citations, ok? So, Barlow made an impact on my field, but the wider impact of that article was really to galvanize a lot of people in the community who kind of came to understand that copyright – this obscure thing that we didn’t really like to think about – actually had some impact on our lives especially on the Internet. [01:20:40]
So, I wanted to spend most of my time talking about a conference that I was at, in Amsterdam, in the summer of 1996. And one of the keynotes of that conference was John Perry Barlow and consistent with “The Economy of Ideas” article, he started talking about the vision of the digital future as digital information was vaporous cargo, which exists either as a pure thought or something like thought, voltage conditions, darting around the net at the speed of light. Copyright might have made sense to thrive in the analog world, because Gutenberg notwithstanding, it was still hard to make a book. But copyright in the digital era, he thought, just didn’t work at all. [01:21:35]
And he spoke of efforts to keep the sinking ship of copyright afloat as taking three forms:
(1) A frenzy of deckchair rearrangement.
(2) Stern warnings to the passengers that if she goes down they will face harsh criminal penalties.
and
(3) Serene glassy eyed denial.
The other keynote speaker at this particular conference was Bruce Lehman, who was, at the time, the Head of the Patent and Trademark Office, and the Chief Intellectual Property Officer for the Clinton Administration. And he had just published this white paper on intellectual property and on the Internet, in which every temporary as well as permanent copy of any copyrighted work anywhere had to have permission in order for those digital copies to be made. An ISP should be strictly liable for every infringement of users, they would have a responsibility to monitor everything in everybody’s files, in order to make sure that there was no infringement, and everything was going to be a locked up. There was not going to be any fair use anymore. We don’t need fair use, because everything can be licensed. And this kind of heavily proprietary really really locked down everything approach was scary because this guy was the head of the government in charge of this particular policy. OK? [01:23:02]
So what we needed was a poet to galvanize and to make us all really understand and appreciate what was an alternate future to that which Bruce Lehman was setting out for laymen. Barlow was a dangerous charismatic anti-Christ. And for Barlow, Lehman was the captain of the ship that was sinking, of copyright, and so having these two people go at it was really one of the things to really remember.
Now it’s important actually that John Perry Barlow’s essay about this new economy, and the speeches that he gave, really did galvanize a lot of organizations and a lot of people, to become copyright activists. And I think that was a really important thing. Part of why was so different was that civil liberties organizations typically have thought “Oh copyright doesn’t matter, it’s a business law subject. It doesn’t have anything to do with us. And Barlow really got that copyright had a civil liberty dimension that we all really needed to appreciate, and we needed to make our voices about what copyright should do available to the world. [01:24:24]
So a favorite passage that I have from him about that is:
“When the primary articles of commerce and society look so much like speech as to be indistinguishable from it. And when the traditional methods of protecting ownership have become ineffectual attending to the problem with broader and more vigorous enforcement will inevitably threaten Freedom of Speech. The greatest constraint on your future liberties may come not from the government, but from the corporate legal departments laboring to protect, by force, what can no longer be protected by practical efficiency or by social consent.”
I think these kinds of words really inspired those of us connected with EFF, to really go out there and defend fair use. To defend our Freedom of Expression. To push for policies that were much less awful than the policies of Bruce Lehman was going for and if you think that copyright isn’t in too bad shape today, it’s partly because that galvanizing, which Barlow was part and parcel of, really worked. [01:25:32]
And the positive values of sharing have inspired so many other organizations, and I think it’s important to say: Many of you out there use Creative Commons licences, you enjoy the sharing of content, and John Perry was there at the launch of Creative Commons and it is now global and millions and millions of people use it, and it’s part of his legacy too.
So thank you and let’s celebrate his life.
Cindy Cohn: Well it’s my great delight to stop trying to pretend to be Cory Doctorow because Cory is here.
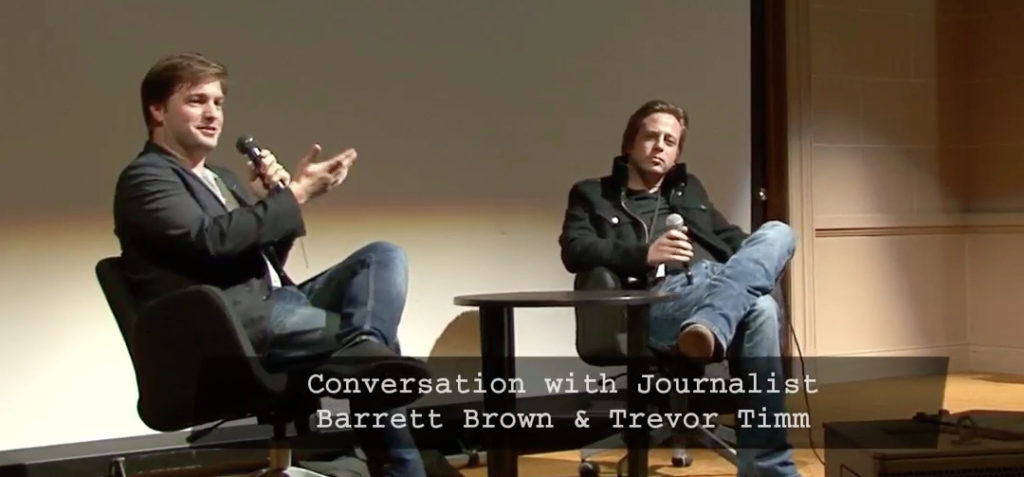
Cory Doctorow: Sorry. There’s only one runway working in SFO today. So, they held us in Burbank for several hours this morning, but I’m very glad to be here in time to introduce Trevor. [01:26:51]
So, Trevor works with Freedom of the Press Foundation, which has many different projects that it works on, but the one that I thought I would talk about today, in the context of Barlow’s work, is the tooling that they do, cause Freedom of the Press Foundation distributes an important tool; refines distributes and supports, an important tool, called SecureDrop – that allows sources – anonymous sources – to contact journalists in a very secure way, in order to report on wrongdoing and blow the whistle.
So obviously, this has some relevance to some of our speakers today, but to me, the most amazing thing about what SecureDrop does, is it is it exemplifies the way that software is a different thing in the world to the kinds of things that we’ve used in our interventions in the world before.
It’s been observed that many people around the world, billions of people, struggle under bad code written by callow Silicon Valley dude bros who hack up a few lines of code and then subject billions of people to its outcomes, without any consideration of the ethics, and when we talk about that, we missed the corollary, which is that programmers who want to do something good for the world, can sit down and encapsulate their expertise. Create the self executing recipes that allow everyone to share the benefit of that expertise. [01:28:07]
It’s a new kind of tool. Not like a hammer where, with enough time and patience, you can learn to drive a nail as well as the person who perfected it. But more like a genie; where once it’s been created, other people can take advantage that technical expertise. And so this is an amazing thing that’s a thing I think Barlow got about what the future held for us. A world in which some of these gaps that seemed unbridgeable, when the tools were crude and difficult to use, could become things that would bridge themselves, through the interventions of ethical technologists.
And so with that I’d like to hear Trevor today.
Trevor Timm: Thank you Cory. So, I have some slides here, but these aren’t them. [01:28:56]
Cindy Cohn: This is, by the way, I’m sorry this should have come up before, and I really want it. Can you go back to that?
Trevor Timm: Sure.
Cindy Cohn: This is Pam and Barlow and Bruce Lehman at the event. They all look – Lehman is faking is, but the two of them look really happy.
(From the Audience): “What’s your last name?”
Trevor Timm: Timm.
So, I just have a couple slides I wanted to show here. So my name’s Trevor Timm. I had the honor and privilege of co-founding Freedom of the Press Foundation with J.P. Barlow in 2012. Here you can see him with one of our other co-founders, Daniel Ellsberg. [01:29:45]
And so, when we founded Freedom of the press Foundation, I had just started a job as an activist at EFF, and like many other people who worked at EFF, and in this room, I looked up to Barlow as kind of this mythical hero. But you know, as soon as you meet him, just like every single other person who’s ever met him, quickly you think that you’re his best friend and so he was really our guiding light when we first started. He was the organizational powerhouse that brought together people like Glenn Greenwald and Laura Poitras and John Cusak and Dan Ellsberg to help start our organization. And, on the day we launched, he wrote an article for The Huffington Post. And the quote I’m going to read I think describes our beliefs better than I’ve heard before or since and the quote is “When a government becomes invisible, it becomes unaccountable. To expose its lies, errors, and illegal acts is not treason. It is a moral responsibility. Leaks become the lifeblood of a republic.” [01:31:00]
And this article was called “Crowdfunding the public’s right to know” and you’ll see the phrase “the public’s right to know” in a lot of Barlow’s writing about a lot of different contexts, but in our context it meant that the press freedom was not just about protecting the journalists doing the reporting or even just the whistleblowers who get information to the reporters, but the public at large. All of this is in furtherance of our ability to know what our government is doing behind closed doors under our name, and it is the the quintessential idea behind what we had wanted to do from the start.
And so one of the things that we wanted to do was inspire a new generation of whistleblowers: A new generation of Daniel Ellsbergs, which is what Barlow was trying to get across in that piece. And so the date on this tweet, which is the day that we launched, is December 16th 2012. So, a couple months later, unbeknownst to many of us apparently at least one person had heard this call. And so an unnamed government employee, got in contact with one of our first staffers, Micah Lee, who then connected him with two of our board members Glenn Greenwald and Laura Poitras, and less than six months later, everybody learns the name Edward Snowden. [01:32:39]
And so this is the first tweet that Barlow tweeted about Edward Snowden on the day, June 9 2013, that everybody learned his name for the first time. Over the preceding weeks and months, Barlow would become Snowden’s most prominent and vocal backer in the press. He must have tweeted literally hundreds of times about Snowden, defending him from all angles. This was at the time where the Government’s smear machine against Snowden was at its all time peak, and he was taking on each and every one of these criticisms, and really gave space for a lot of people in the civil liberties community and elsewhere to understand the importance of what Snowden did.
` I actually wanted to go back and scroll through all of the tweets but taking screenshots was literally going to take me an hour. I mean, right now we’re only like three weeks in since the last known revelations, and they they keep going for pages and pages and pages. And so you know, there’s a lot of things that I’m going to remember about Barlow, but what I think about most, was that it was not just theoretical for him; it was not just him saying these words, and then, when the going got tough, you know, kind of backing off. He relished that fight. And because of his advocacy around this subject, Edward Snowden came forward. But also, he taught everybody that you know what it means to stick up for the public’s right to know. And so with that I will kick it over to Edward Snowden. [01:34:55] (Shot of audience.)
Edward Snowden: Thank you. (Applause.) I’m never going to get used to this. (Standing ovation at the Internet Archive)
There are a lot of things that can be said about John Perry Barlow, or, as I called him, JPB. He was a good man. He was a brave man. He was an orginal thinker. This was an incredibly talented charismatic individual.
He had no obligation to live a life that was touched by the struggles and challenges and politics that we’re made to deal with and confront every single day. For many of us, it’s not a choice. We have no alternative. We have no special talent. We are not rock stars. But he chose to side with us. He chose that. And it is that shrewdness that I think is the mark of highest distinguishment for his character.
This was a man who actively sought discomfort when he had every opportunity to sort of stay in bed with the wonderful and interesting people that were involved in his life, and he never lost this. In fact, as he got older, in the brief time that I knew, and I had the rare opportunity to share a stage with him, he became ever more politically involved. Ever more politically astute and ever more self-sacrificing.
This was a man who was not afraid to say things that others were not. This was a man who was not afraid to ask questions that would make people uncomfortable, and yet were necessary. And it was this trait that he put into the organization and lives that he was connected to that brought be forward. [01:38:25]
One of the stories that is very little told in the media, perhaps untold, is this story: I’m sitting at the NSA, as a high school dropout being paid an extraordinary amount of money to help build and run machines to spy on you. And there were over 30,000 people working at the NSA at the time. This was a comfortable life. This was an easy life. And it was certainly the path of least resistance for me. [01:38:58]
Now I started out as a true believer. I too, had a choice, but as I climbed higher and higher levels of the government. As I gained access to more and more highly classified information. And eventually, I reach the sort of highest peak of security clearance. I realized that something wasn’t right. I realized that what was legal was not necessarily what was moral. I realized that what was being made public was not the same what was true. And eventually this reached the point where we had the most senior intelligence official in the United States government, General James Clapper, who went before Congress, a sworn an oath to tell the truth nothing but the truth. You know we’ve all heard it. And he was asked by Senator Ron Wyden: “Does the NSA spying on millions, or hundreds of millions, of American’s communications.” The general immediately starts sweating, rubs his head, realizes he’s on camera. Thinks about it for a second. He’s gotten these questions 24 hours in advance. And he says “No. No sir. Not wittingly.” [01:40:20]
This was a problem that John Perry Barlow understood, even though he didn’t know exactly how that was a lie. He knew it didn’t sit right. And he talked to me about this after the fact, after I had come forward. But the idea here is this story 2013 of the mass surveillance revelations was never about the surveillance. It was about democracy. What does it mean that when we have a system of government. We have elected officials. When we have the highest powers in our country accountable the lowest standards of behavior. At the same time if we break the smallest law, as ordinary people, we face the highest consequences.
Well JPB created this organization, The Electronic Frontier Foundation,with his friends. He created the Freedom of the Press foundation, that I would later join myself and have the privilege of serving on the board with him, alongside. And the idea is this. It’s a question that actually an argument that he put to me when I shared a stage talking about the future of democracy, with him, before an audience. And I was talking about sort of where I thought the systems were breaking down; where things were working, and where they weren’t working. And what sort of problems, in a very technical sort of engineer’s way, because I’m not a politician by training. And he said really that he thought I was missing in the point. He said in the unique case of these United States the whole question of national security, this entire area of conversation topic, is being misrepresented by the government to the detriment of the public. “National security” doesn’t mean what they try to make you think it means. “National Security” is not about terrorism. “National security” is not about military. [01:42:35]
“National Security” means the security of our founding principles. It’s not our borders. It’s not our culture. It’s not anything except those founding documents that we still profess to believe in. According to him. And if we are insecure in our beliefs and our willingness to protect and preserve those beliefs, that is a threat to national security, and perhaps the only one that matters. Now I’m not even sure he knew this at the time, but when I was going about my sort of dark work at the NSA gathering information about crimes against the public on a previously unprecedented scale, I was wearing a hoodie from the Electronic Frontier Foundation. It was a parody of the NSA. When I came forward, the very first photograph that was made public of me in Hong Kong, where I was meeting with journalists, to provide them this material, which then I lost access to. Because, I didn’t want to be exploited. I didn’t want to be the person who’s making the choices of what should and should not be made public. I felt this was the role of the fourth estate. This is the proper function; the necessary purpose of press in a free society. To contest the government’s monopoly control of information. As much as it’s wonderful when hackers go out and get this information for us, and as much as I think it is necessary for whistleblowers to share with us the information that we need to know, I wasn’t elected president of disclosure. And I don’t think anyone else is either. This is why the First Amendment is first. [01:44:37]
In every free society, the legitimacy of government derives from a single principle; the consent of the governed. But that consent it only meaningful if it’s informed. What happens when we cast votes for politicians who claim certain campaign promises, and then, not only do they not deliver on them, they actually expand the surveillance programs that they pledged to terminate. And this, because I’ve gone on for a while here, is that part of John Perry Barlow’s sincerity that I admired. And this is the reason, ultimately, that led me to many of the choices in life that I have made.
When I was a young man. I was reading his Declaration of Independence of Cyberspace, and perhaps that may have been that seed of radicalization. I’ve said before that I used to work for the government and now I work for the public. I’m not sure JPB ever had any other allegiance. His love was for all of us. This is why he spent that long life could have been so comfortable. So frictionless. Constantly searching for the next thing. Constantly searching for the next struggle.
He told me on that same day. On that same stage. One of the things that he struggles with, is people who turn away. People who don’t think. People who are so in love with comfort that they forget that struggle is what drives us forward. He shared with me a saying that he says he got from the Navaho, which is the kind of thing that only an interesting guy like him could just pass off as a throwaway comment: “You can’t awaken somebody who’s pretending to be asleep.” [01:46:39]
John Perry Barlow woke me up. He raised a message sounded an alarm, that I think we all heard. He didn’t save the world. None of us can, but perhaps he started the movement that will. I want to thank him for everything that he did for me, for us, for the United States, and for this world. He was an incredible person. He was an inspiration to me and it was an honor to have known him. There is one thing that I I’d like to say from him, which I will keep with me for the rest of my life as I think about what comes next for myself and hopefully those of you in the room as well. [01:47:28]
I said when we’re looking at all of these problems that face the world today, that face our politics today: the partisanship, incivility, the inhumanity, the injustice that fills every conversation and we try to make for the people who are in power confront that and fix it to do their jobs. I struggle with the question of how it is that we correct this. What it is that we’re supposed to do, and why it is that they feel so comfortable. And it came down finally to this feeling of immunity. Of unaccountability that these powerful institutions all seemed to enjoy. It didn’t matter whether it was the Attorney General breaking the law. It didn’t matter who was the CEO of Citibank breaking the law. They had a different standard behavior. And when they saw the world. When they saw the system. When they saw how much control they had and how little we had. They said well what are you going to do about it.
And he sat, and he thought. Just a long pause on stage in front of so many people which is the kind of thing that only somebody like him could really get away with. I know I personally feel obligation to fill the silence. Then he said “The United States such as it is today exists to look at precisely that claim. “What are you going to do about it? And to answer that question, and to answer it right.” [01:49:18]
Ladies and gentlemen the life of John Perry Barlow was an example to everybody. Thank you very much. Thank you.
Cindy Cohn: (Explains process of writing questions on note cards). In the mean time, since we didn’t get to get Cory’s opening remarks, while you guys are scribbling, I was going ask Cory to say a few words, and then we’ll jump into the Q and A. [01:50:56]
Cory Doctorow: Sure. I just want to say a very few words, and I said some of them were in my introduction for Trevor.
We are in awed moment right now for people who care about this stuff – that Barlow campaigned on – that the EFF works on. Because for 30 years, we’ve been rattling the cages and shouting “these computers and the networks that connect them – they matter!” If we get them right, things can be great but if we get them wrong things, will be terrible.”
And now we’re living in this bizarre moment of the Techlash, where, at long last, people are saying “we’ve got computers horribly wrong and they’re terrible. Why didn’t you idiots warn us!?” (Laughter) [01:51:30]
And you know it’s OK. I’ll take what I can get. There’s a moment at which your tactics change, if you’re an activist. It’s the “moment of peak indifference.” When the number of people who care about your issue only goes up forever more. I mean yeah we spectacularly failed to get people to care about privacy and the destiny of the Internet for twenty five years, and that is a catastrophe. We have carbonized our atmosphere with personal information that will never go away and whose effects will be felt for decades to come and the only thing worse than that, would be to let it go to waste. To let this moment in which people realise that there’s a problem slip away from us, instead of saying not only did we know this stuff was going to happen but we can do something about it. [01:52:20]
And so for EFF, for Barlow, for the people I see here today old friends and people who I recognise from so many different contexts. I feel like this is our mission. It’s to make the world safe for technology but more importantly to make the technology safe for the world. To seize the means of information the way Barlow taught us to. Thank you. [01:52:42]
Cindy Cohn: All right we have a few questions from the audience. Feel free to keep writing. There are a couple of these, folks, I may save for the second panel, because I think I have people who may have a better better perspective on them, so don’t worry about that. [01:53:05]
I guess the first question is for any of you really. What do you think Barlow would say about the Facebook revelations of the past week?
Trevor Timm: Well he would laugh, like he laughs at everything. The thing about about Barlow was that he would, actually this was he would sometimes infuriate us, at EFF or Freedom of the Press Foundation, because he always liked to talk about how he lived his life totally public and transparently. But, at the same time he understood how much other people really cared and valued their privacy. I think that he would he would probably launch into a story about how Sean Parker used to sleep on his couch and that this might have been all his fault.
Cindy Cohn: Now this one could go on for a long time, but maybe just pick one example. What did you and Barlow disagree about, and how did you work it out? Yeah, Mitch might be a great one for this. [01:54:34]
Mitch Kapor: We really disagreed about whether government could have a constructive role in addressing some of the considerations to get appropriate (Stops. Thinks.)
Well, look at it this way: I thought there was a place for appropriate regulation; public policy around telecommunications and infrastructure, and led EFF on a death march to Washington D.C. and its early days, to try to bring that about. And John, at that point, was a pretty resolute libertarian; the less government the better. I lost that battle entirely, both in D.C. and how it was resolved and EFF became, and was, staunchly libertarian. John Gilmore and I and others, in that phase of things. So it was only later that I came to understand that really the only thing that liberals and libertarians agree about is civil liberties. On pretty much everything else, they’re on you’re on opposite sides. Nonetheless, the fact that we disagreed didn’t reduce the intensity of feeling we had for each other. [01:56:10]
Pam Samuelson: I will say John Perry Barlow and I – we disagreed about copyright being dead. Lots of people wanted it to be dead. And I said “I’m sorry. OK? We really have to adapt it. And so I think the adaptation that EFF has worked on very assiduously has been consistent with copyright at least not being a source of oppression. Except unfortunately in the case of Aaron Swartz. We lost that battle and that was a really bad one, but I think if you kind of think about copyright; it’s not as bad as it could have been. And John Perry and I agreed on that. But it ain’t dead. [01:57:04]
Cindy Cohn: Here’s another one. “We seem to be at a tipping point in our collective understanding of the Web plus the fear and the risk at a high. What comes next to steer us towards the better?”
Trevor Timm: That’s a tough one. I think that’s a Cory question.
Cory Doctorow: To be honest. I was just thinking as I got up here this is the third time in about 12 months that I’ve been on this stage, and I realized I’ve answered this question every time, so it would be a shame if I passed it up this time.
So, as a science fiction writer I’m keenly aware of the fact that I have no business predicting the future. We suck at it. Thankfully, science fiction writers sometimes pretend to be fortune tellers, but they only get there by by being Texas marksmen: They fire a bunch of shotgun pellets and then draw a target around the place where they where they hit the side of the barn. If some science fiction predictions haven’t come true would be more remarkable than that none of them came true. [01:58:06]
But the reality is that the future is not predictable; it’s contestable. So what happens next is the result of what we do, not the result of some ineffable unstoppable historic force that we are passengers in, and even if there are historic forces that act on us they are the result of individual actions that people took in earlier rounds of the game that we’re playing now.
And so, for me, rather than being optimistic or pessimistic, which are about making a prediction the future will be better it’ll be worse. I try to be hopeful, which is to take the position that you can do something to materially improve your situation. And from that new vantage point you might find some other action that you could take to materially improve it.
And if you’re a software developer if you’ve done a little CS you’ll recognize this this is “hill climbing.” This is what you do when you need to traverse a landscape whose contours you don’t know and can’t know and will likely change before you do know them. And instead of trying to know the whole terrain and then solve it, all you do is you pretend to be an ant with your forward facing eyes that can’t look up and see where the hills are but you have all these legs, and they’re resting on uneven terrain, and you ask yourself Which leg is on the highest terrain, and you take a step that way. And then you survey your legs again and again and again, and you climb step wise to the highest peak you can reach.
And I don’t know how we get to a better world, but I know how we can make this world slightly better. I know that if we could push back against the forces that are trying to make it harder to defend ourselves technologically from surveillance, we will maintain a technological space where we can organize politically to protect ourselves from surveillance, and that within the act of teaching each other how to protect ourselves from surveillance, we will make a normative change and teach our friends why surveillance matters. Because privacy of course is a team sport. It doesn’t matter how great my opsec is if you’re holding all of my data that I’ve sent to you on a Google server.
And that between us, maybe we can make a market for privacy too. Maybe someone out there with stars in their eyes will raise capital on enhancing our privacy rather than taking it away. And maybe once we’ve done some little step towards that we will find something new that we can do that will improve things because the first casualty of every battle is a plan of attack. We can sit here and try to spin scenarios till the cows come home and not get anything done. But we can roll up our sleeves and do something. [02:00:33]
Cindy Cohn: This is a question for Mitch. “You describe beautifully the moment when the hackers and the DOJ shook hands. Can you describe a moment that you and John had that frightened you?”
Mitch Kapor: Yeah I alluded to it. We were invited into the CIA, this is early days, to just talk about the issues that we were we were working on. And in Langley, in the headquarters. I’ve never been there. I don’t think John had ever been at that point. And it’s this big fortress and there are lots of signs about no recording devices and turn everything in. And John and I conferred and we devised a plan. We said “well, can we bring in our laptops?” This is in the early 1990s. Yes, actually if you check the laptop, (they said) you can bring your laptop.
Our laptops were recording devices. This was brand new at that point that our Macs had mics in them and audio capture software and this wasn’t a common thing and we said to each other “I wonder if the CIA knows this?” [02:01:50]
So we were scared. And they didn’t know that. And we went in and recorded the meeting inside the bowels of the CIA. Quite illegally. We thought of it as a sort of science experiment. I mean, we didn’t just want to make claims that the government was cluefull or clueless. We wanted to see. Since they made such a big point about the security saying you know understood that Mac duo had a…and they didn’t. But we were pretty nervous going in. That’s a true story!
Cindy Cohn: This is a question for Pam, and the question is: “When we’re thinking about copyright on the internet, how do we protect songwriters?”
Pam Samuelson: So, John Perry Barlow obviously cared about that a lot too. And I think that if you go back and read The Economy of Ideas article again, as I did in preparation for this, you’ll see that he cares about that question. About how to protect songwriters. About well, you know, how are we going to be able to to make a living? [02:03:18]
And I think his experience with the Grateful Dead meant that performances were going to be very important, and relationships were going to be very important, and interactivity was going to be very important. And so, I think that there are there are musicians who are forming relationships with people who love their work. And there are lots of live concerts going out there. But of course that’s not the only revenue that that songwriters want to have. And I think copyright actually works pretty well to protect songwriters. It’s just that there would obviously be more compensation going to them if Congress would actually change the law so that a bigger revenue stream from some of these digital services would be going to the to the songwriters and to the performers and not just to the recording industry.
Cory Doctorow: Can I weigh in briefly on that? So Pam takes a backseat to no one when it comes to understanding the copyright laws. So it in no way do I do I claim to have any expertise that Pam lacks. But I wanted to answer from the perspective of someone whose majority income comes from selling copyrighted works, and to say that I think that the original sin of copyright and the Internet is that because the way we figured out whether or not you needed to pay attention to copyright was whether you were making or handling a copy of a work, and because everything we do on the Internet involves making and handling copies of works, because everything on the Internet is done by copying. We decided that this esoteric branch of entertainment law should be the major source of regulation for the nervous system of the 21st century. And, you know, I think one of the great problems that we have, the tensions that we have, in copyright right now, is that; As good, or potentially good, as copyright might be for regulating the relationship between labor and capital in the entertainment world, “songwriters and labels” or “writers and publishers,” that it’s practically no use at all in regulating my relationship with my audience. [02:05:27]
If you have to understand copyright to read one of my novels, then something is terribly awfully wrong. Right? That doesn’t benefit me and it doesn’t benefit my industry.
And so I think that we can really split this into two problems. The first is: “how do we make sure that our industrial regulation is contained to our industry and doesn’t metastasize into regulating 12 year olds writing fanfic in their parents basements?” and then the second question is “what rules should we have in our industry?” And it’s much easier to answer that second question, if we’re not pretending that those rules are also going to govern everything else we do. That involves computers which these days is everything.
Cindy Cohn: By the way Mitch – one of the questions was “Where can we get a copy of those tapes?” [02:06:20]
Mitch Kapor: Patience patience. I have 40 years of old stuff that is being cataloged and when I turn it up that will be when? In process.
Cindy Cohn: “One of Barlow’s super powers was his ability to move between worlds and bridge seemingly vastly different contexts. What was your favorite memory of him doing this?”
Trevor Timm: Well so, you know, I mentioned in my initial talk about how you know all the staffers in effect kind of considered him as this mythical hero. And part of the reason was because… So there’s board meetings every quarter. And so that’s when the board members come in obviously. And we never knew if Barlow was going to show up or not. He almost always did, but it was always a half hour late. Two hours late. Ya know, to the point where, later, at the Freedom of the Press Foundation, we would tell them the board meeting started like 2 hours earlier than it did. So hopefully we’d get him there close to on time.
So we would all we would always be waiting around to get a peek at him. And when he would inevitably show up, he would always have the most fantastic excuses imaginable. To the point where nobody could ever be mad at him. He say “oh I was I was in a argument with Bob Weir; I couldn’t leave Mill Valley for an hour.” Or, ya know “Yoko Ono wouldn’t get off the phone with me.” And so. He has he has a memoir coming out a couple of months. that he actually finished just a couple of weeks before he passed away, and it’s fantastic and I would recommend everybody read it. It’s called “Mother America Night.” But I was joking to Cindy the other night. I really wish it was called “Why I was late.” [02:08:09]
Cindy Cohn: We only have a couple of minutes left. So actually, I want to ask this question. The first question is: “What can every person here do today here today do to best honor John Perry Barlow?”
Mitch Kapor: One of John’s most special qualities is, no matter how dire the circumstance. In fact, the more dire the circumstance, the more he was able to see the good in people and the good in all of the actors on all sides of whatever dispute was involved. I would encourage people to regard that as an exemplar and to cultivate that in their own lives by whatever means you find efficacious. [02:09:19]
Thanks our first panel for a minute take a break people please go ahead. There are amazing people in this audience, just by my scanning them. Talk to a stranger; ask them how they know Barlow. Chances are you’re going to hear an awesome story.
One last thing I want to thank, and I saw that he arrived a little late. Eff’s own Hugh D’Andrade designed this amazing Barlow, and we put it on a T-shirt, and they’re available outside. So if you want one please do. They’re probably going to be limited edition, so this would be a good time to pick it up if you want to. I don’t know. We didn’t really make the Snowden goodies after Mr. Snowden showed up, but often these things rolled forward instead of backwards. So take a chance, meet a stranger, and come back in 20 minutes and will we’ll be off on the next the next set. [02:10:30]
PART TWO (Begins 02:46:10)
Cindy Cohn: All right thanks everybody. I hope you get a little refreshment. A little break. A little chance to talk to somebody interesting because this is an extremely interesting group of people. I’d like to invite the second set of speakers to come up, if I may.
Our second panel of speakers are Shari Steel, John Gilmore, Stephen Levy, and Joy Ito. And although she ended up at the end, our first speaker up is Shari Steele.
Cory Doctorow: So Shari was the turnaround specialist that turned the EFF into the powerhouse it is today. She calls herself a “First Amendment Junkie.” And when I met her, EFF was on the rocks. John Gilmore had brought it back to San Francisco from adventures on the East Coast and they lost their digs and so they were everyone was working out of their living rooms and meeting up once a week in coffee shops and today. Well, today we’re a much bigger organization and a lot of it – well so much of it is due to Shari and her leadership. One of the places where I got to see her shine is in managing her Board, and it’s quite an irascible and amazing board. And as you heard about Barlow, he was always a challenging board member. So I’m looking forward to hearing what Shari has to say about about being the adult supervision for John Perry Barlow. [02:47:56]
Shari Steele: Hmmm. I wasn’t going to say anything about being “the adult supervision of John Perry Barlow.”
So, I started EFF in 1992, as a staff attorney, and I’m just going to give a little aside. Mitch Kapor actually detoured his plane to stop to meet me too. (Laughs) I was in Washington D.C. and I had already interviewed with Jerry Berman and Danny Weitzner, who at the time were the EFF D.C. office, and Mitch wanted to meet me and so was on his way back to Boston from someplace or other, and stopped so that I got to meet him. And I got the job. So whatever, but when I first when I first took this job we didn’t know what EFF was going to become, but I had heard of Mitch Kapor and was really interested in working with Mitch Kapor, but had never heard of John Perry Barlow. I was not a Grateful Dead fan I was not from San Francisco. I didn’t know who this guy was. It literally took one meeting for me to become a groupie. This man had more charisma than anybody I’ve ever met and his belief in the First Amendment and in a free speech, in a society with free speech ,and a vision of the Internet as being a place for free speech, resonated so powerfully with me that he became an instant buddy.
Our first real big fight related to free speech was in 1995, when Congress passed this horrible horrible law called the Communications Decency Act, or the CDA. Barlow was, and we were all, really upset about it. As soon as it passed, we knew that was unconstitutional. And, with the ACLU, EFF challenged the law. [02:49:50]
The big part of that that was horrible was the part about indecency. It was it was Congress’s attempt to regulate pornography. And in it they had this whole part about if, basically, if the internet was was not good enough for kids then it was bad. So things like, talking about sexuality, or curse words, or talking about assisted suicide. Talking about anything that would be a topic that wouldn’t be appropriate for kids, you could possibly have been fined two hundred fifty thousand dollars per violation for doing that on the Internet.
So along with this lawsuit, and that was, of course, the EFF and ACLU way of fighting it. John Perry Barlow in his way of putting pen to paper, or typing on the keyboard, came up with his Declaration of Independence of Cyberspace. I loved this thing from the very start. Cindy and I were just talking about this the other day. [02:51:04]
So I re-read it particularly getting ready for today. A whole bunch of this was about sovereignty. The way he wrote it was was basically daring governments from around the world to come in and regulate cyberspace and saying “you have no business here.” But the reason why I loved it was because the reason why he felt that cyberspace was so important to defend was speech. It was about the free speech. And here’s a quote from the declaration:
“We are creating a world where any one anywhere may express his or her beliefs no matter how singular without fear of being coerced into silence or conformity.”
As a first amendment attorney yes as a first amendment attorney those those words still still give me chills. So in 1997, those indecency provisions of the CDA were declared unconstitutional by the Supreme Court. Yay us. And ten years later Barlow, was asked to defend or talk about his Declaration of Independence of Cyberspace. And he kind of talked a bit about the sovereignty your stuff but he gave us some more beautiful language that I’m going to share with you here. [02:52:27]
“I still dream of a world where anyone could express anything he or she chooses, no matter how odious or unpopular, without fear of official reprisal. I dream of a world where anyone else can either here or ignore those expressions as they choose, but will at least be able to make that choice with similar immunity. I dream of a world where anyone who wants to know something will be able to learn the truth about it, regardless of his or her economic status, social standing or race. I imagine a future where intelligence will be the primary economic resource and the location of one’s cerebral cavity will be irrelevant to the earning potential of its contents. I have not given up on the idea that as a species we can be more humane and fair. Nor have I forsaken the notion that the greater understanding bred by universal access to knowledge is the key to increasing these qualities in us.” [02:53:30]
Yeah. And that’s the thing about Barlow. He wanted to hear all different kinds of viewpoints. He knew more people who had divergent ways of looking at things, because that’s how he grew. That’s how he thrived. He was always learning. He always wanted to know more. He was always encouraging voices. He was always encouraging people to talk to each other. To have conversations where you normally wouldn’t maybe have thought that this was somebody that you might have something in common with. He was fascinating, and he was dynamic, and he helped us create an Internet that has all sorts of fascinating and dynamic speech in it. Thanks. [02:54:23]
Cory Doctorow: So our next speaker is John Gilmore. John should need no introduction because of his many contributions in addition to starting EFF, he started, depending on how you count, the first or second dial up ISP, and has written some very key software that you’ve probably interacted with today and everyday of your life for the last 15 or 20 years. If you’re even a moderate technology user and I imagine most of yours are heavier than that.
But for me the thing that kind of sums up Gilmore is a phrase he’s well known for. A phrase that’s actually gone beyond him, that “The Internet interprets censorship as damage and routes around it.” And the first time I heard this, I thought it was by way of a prediction about technology. That our technology could route around censorship in this kind of automated way. And what I realized, when I actually sat down and talked to him about it, as he was describing the thing Usenet administrators used to actually do, where they would sit down and go “you can’t censor me I’m going to route around you using these anti damage protocols that we’ve developed.” [02:55:36]
And what he was talking about is the culture that was present at the birth of the Internet. A kind of a mixed bag of a culture, but it had this strain in it of people who felt a kind of civic duty to the Internet. To keep it to a place where we could have this society of the mind. Where we could come together across borders and across interests and across different points of view, in this very Barlovian way. And when I realized that that’s what he was talking about not that we’d build some technology that could recognize censorship and right around it but that we built a culture committed to doing that. That I knew that we were on to something important. [02:56:15]
Jo John Gilmore: Thank you.
There are probably 25 million Americans who have taken LSD. They would, if hard pressed in private, also tell you that it profoundly changed their lives, and not necessarily for the worse. I will readily grant that some of these are hopeless crystal worshippers or psychedelic derelicts creeping Oregon woods, but far more of them are successful members of society: CEOs, politicians, ministers and community leaders. This is true whether we want it to be or not, but the fact that so few among those millions dare utter this truth is, in a supposedly free country, a symptom of collective mental illness.
Now that the worst of the war between the 50s and the 60s may be over. Perhaps it may become possible. Many people may be able to do as they ought to have done decades ago. Like the peculiarly honest Steve Jobs and the peculiarly lucid John Perry Barlow and the peculiarly persistent Rick Doblin and the merely peculiar John Gilmore, and say in public there was a moment years ago when I took LSD, and whatever the immediate consequences, it made of me a different person than I would have been, and different in ways I have been grateful for all this time. By the way, everything I’ve said so far is literal quotes from Barlow, just slightly rearranged. [02:58:14]
And so is this: “One can make a non-ludicrous case that the most important event in the cultural history of America since the 1860s was the introduction of LSD. Before acid hit American culture, even the rebels believed, as Thoreau, Emerson, and Whitman implicitly did, in something like God given authority. Authority, all agreed derived from a system where in God, or dad or more often both, was on top and you were on the bottom, and it was no joke. Whatever else one might think of authority; it was not funny. But after one had rewired one’s self with LSD, authority, with its preening pomp, its affection for ridiculous rituals of office. Its folsom grandiloquence and eventually and sublimely its tarantella around mutually assured destruction, became hilarious to us, and there wasn’t much we could do about it. [02:59:32]
No matter how huge and fearsome the puppets, once one’s perceptions were wiped clean enough by the psychedelic solvent to behold their strings and the mechanical jerkiness of their behavior, it was hard to suppress the giggles. Though our hilarity has since been leavened with tragedy loss, and a more appropriate sense of our own foolishness; we’re laughing still. LSD is illegal primarily because it threatens the dominant American culture. The culture of control. Well that’s what Barlow thought, and after studying how to end the drug war for a few decades, I tend to agree. I think that Rick Doblin’s approach is the most promising path toward ending the collective mental illness that Barlow diagnosed. Rick is using psychedelics in FDA approved clinical trials, successfully treating traumatized, out of control women and soldiers, bringing them back into self control. This is gradually removing psychedelics from the counterculture and making them less threatening to the culture. [03:00:51]
Now, one of the classic experiences that happen when people take psychedelics, is to have the experience that “all is one.” It’s a feeling of unity with everyone and everything. A feeling that you and I, and God, the rocks, and the trees, and the stars; are all the same person. The same thing. And not just made of the same stuff but literally the same.
You can find echoes of these experiences throughout our world. The the Indian namaste that salutes the divinity in another person. Thou art God, from Robert Heinlein “Stranger in a Strange Land.” The All One” of Jewish soap maker Dr. Bronner, which he hoped could heal the world against future holocausts. Barlow knew this oneness well. He seemed to embody it much of the time.
In speaking to a women’s gathering, Barlow said, “Anytime you’re more in touch with the unity of all things, your chances of having a positive approach to the world are enhanced.” [03:02:03]
And right here is where Barlow’s psychedelic philosophizing merged with Barlow’s Internet philosophizing. In a 1992 keynote speech to the Usenix association, Barlow said earlier in the 20th century the French philosopher and anthropologist (Pierre) Teilhard de Chardin wrote that evolution was an ascent toward what he called “The Omega Point” when all consciousness would converge into unity, creating the collective organism of mind. Whether or not it represents Teilhard‘s vision, it seems clear that we are about some great work here. The physical wiring of collective human consciousness. The idea of connecting every mind to every other mind, in full duplex broadband, is one which for a hippie mystic like me, said Barlow, has clear theological implications, despite the ironic fact that most of the builders are bit wranglers and protocol priests. A proudly prosaic lot. [03:03:13]
I know that when I’ve talked to computer audiences in times past, I’ve had a continuous question and complaint from people in the room. They say, “well you know, you want me to behave as though I were a social philosopher. And, actually what I do is bus architecture. Well, exactly. I don’t think you can expect the social philosophers to understand bus architecture very well for a while, either. So both of those jobs fall to us; the people who understand the basic nature of this very different environment. Now as we build and use the Internet, Barlow cautioned us to distinguish “data,” “information,” and “experience” in ways that are often forgotten today. And he had a 1990s conversation with John Brockman that later Brockman put in a book, and he explained, “data differs from information.” You can gather infinite sets of data with machines. But in order to convert the data into information the human mind has to process that data and find it meaningful. [03:04:25}
That’s the important difference between information and other kinds of products. Products of the physical world are generally themselves regardless of the context. A toaster is a toaster is a toaster. In the informational world however each piece of information draws value from its direct relevance to the area of mind that is finding it meaningful or not meaningful. So then the next layer is “experience,” which also differs from “information.” Experience is the real time interactive relationship between the sensorium and all the phenomena that the sensorium has available to it. Every synapse in my body is assessing my surrounding environment, is in an interactive relationship with it. Is testing it. Is on the alert. Whereas information, in most cases, is something taken from the realm of experience and compressed into a potable format that eviscerates and alienates. Information is like life jerkey; dried up and not terribly communicative. Through information, you can come back to experience the vast set of phenomena that are creating the data in the first place. Experience and the universe itself are intimately bound up with one another. Purpose of the Internet and all its surrounding phenomena is to create a context where experience is universal and the informational reduction is no longer necessary. [03:06:00]
It becomes possible for me to ask questions in real time on phenomena that are taking place where my body is not. If your objective is understanding, you don’t want data. You don’t want information. You want to simulate experience as much as possible, because that’s where understanding comes from. So, in another context Barlow said “I really feel that what we’re essentially doing here is reaching for that point at which human beings become so good at communicating with one another that they would create what would amount to a great collective organism of mind. I think we are going to become such a creature. Perhaps we already are. It is a very different kind of creature than has ever been seen in the universe before. It will be enormously powerful and intelligent and you folks are helping it to be born. Thank you very much. [03:07:05]
Cindy Cohn: Thank you John. And I can’t move past John on to our next speaker without taking a moment to really thank John for all the support he gave John Perry Barlow over the years. You know. You opened up your home to him and you were a constant source of support. I certainly am really grateful that you did that and helped him so much.
John Gilmore: And I’m really grateful. I’m really grateful that I got two and a half years of being able to walk downstairs and go “Hey Barlow what are you thinking about today.”
Cory Doctorow: And for me next to introduce my old friend Joi Ito.
Cindy Cohn: Nope. Steven Levy… although they look alike, so you can see how that would happen. (Audience laughs :-) [03:08:08]
Cory Doctorow: So, did anyone here not read hackers. Just put up your hand. Don’t be ashamed. No. This is wonderful because you get to go and enjoy hackers now. It’s an amazing book and it’s the first of a series of amazing books. I don’t mean to imply that you do your best work behind your anything. Every book is better than the last.
Around the world, people picked up hackers and read it and recognized something of themselves in it. This canonical history where this culture came from. What its birth pangs were like. How it ran up against the limits of authority. How it dodged past them. How it was stopped in its tracks by authority sometimes. All of that came together to inspire, literally inspire a generation of people, who found their way here into other tech centers around the world with that vision of civic duty. With that vision of of a network that was made for people who might be a little odd but people who really wanted a better world for all of us not just another high reward career with a big upside that would make your parents happy. But something legitimately weird and futuristic and amazing and maybe a little dangerous. If those aren’t words sum up John Perry Barlow I don’t know what are. Thank you. [03:09:33]
Steven Levy: Thanks Cory. So, I want to talk about John Perry Barlow as a writer. I first met Barlow at a hackers conference, I believe in 1989. I know it wasn’t after that because later on in 1989, we were together in Candlestick Park when the earthquake hit. But that’s a different story. So, at the time, Barlow told me of his plans to write a book. It was going to be called Everything You Know is Wrong. It was going to be this amazing thing which took the disruption of text and put it into the context of the human experience. Kind of like a “Zen and the Art of Motorcycle Maintenance” that instead of a motorcycle you had TCPIP. And it sounded wildly ambitious but I think Borlow could have pulled it off. [03:10:22}
So we’re here today to talk about Barlow’s ideas. But a big reason that we can talk about those ideas was the amazing way that he expressed them. So Barlow was capable of pulling off a quadruple axle level of nonfiction difficulty and you know, doing things like “everything you know is wrong,” because he was a terrific writer. He was good enough not only to explain what was happening to the out of it Mr. Joneses of the world, but also to encapsulate what was happening. To celebrate it, and to warn against its dangers, in a way that enlighten even the aficionados; the people who really knew the digital world. And to do it in a way where the reading was pure pleasure. So I’m sorry to tell you that Barlow never finished that book. But that’s a different story. But he did write thousands of words about the digital world. Words that helped transform the way we all view it. [03:11:21]
Now of course we know Barlow had a way with words. We know this through his lyrics and those lyrics provided him an entry into all sorts of other worlds. In the obituary I wrote for my friend, when he died. I talked about how he used his status as the junior lyricist for the Grateful Dead as kind of an all access laminate to the concert hall of life. But I’m betting that his major legacy is going to be not only his lyrics, but the words he wrote about the digital revolution and all its glories and its discontents.
So let’s start by his appropriation of William Gibson’s term “cyberspace.” You can see why Barlow would be attracted to the concept. Gibson wrote that cyberspace was consensual hallucination. And John Perry Barlow was never one to turn down hallucination, but he did so much with it. Barlowe used cyberspace as a metaphor that wound up becoming the way we all thought of the Internet and as a matter of fact, the way we did all of our digital activities. Not just in the VR world, where you make up a world like Gibson wrote about, though that too, but occurring in a venue where you went somewhere everywhere. Every time you made a phone call. Made an ATM transaction, or did an online chat. [03:12:42]
So when Barlow wrote about it he took cyberspace and our digital activities from something you did – what you did online – where you were online. And we needed this. Digital technology created an abundance of baffling issues by moving us out of the physical world. A place where we’re all, as Barlow wrote, “floating blind as cave fish.” By viewing online as a territory we can talk about those issues and we can mediate them. So talk Barlow did, and write he did. So Barlow in this realm might be best known, beside the Dead lyrics, for these manifestos he wrote. I know we’ve talked about them today. They were splendidly rendered and they made a difference. My favorite Barlow writings are the ones where he does flat out narrative. Of course the ones like the Declaration of Independence for Cyberspace were terrific. Reading those now though seems kind of like artifacts of history. Signposts of the possible. Not to underplay the straightforward Dylanesque finger he was wagging towards the clueless and the evil in those things. But that’s definitely on his greatest hits disc. But to read those now, you kind of feel like you’re in the opening episodes of The Game of Thrones, where people haven’t figured out yet that winter is coming. [03:14:02]
In any case I do go for the long form stuff. I know from personal experience that writing compelling long form fiction isn’t too easy to do, when your goal is to share complex ideas. Barlow understood that the way to do this was to tell stories and anyone who spent time with Barlow knows that he was a master storyteller. So Barlow would like to take the persona of an every person. Of course not every man or woman hung out with John Kennedy Jr., lectured Steve Jobs on Next computer, or helped elect Dick Cheney to Congress. But somehow, this person with considerable ego, communicated with a cowboy wit, a hick town humility, and Cracker Barrel groundedness. [03:14:47]
And he struck a tone that drew us in closely, campfire style. So it didn’t seem off putting, when he tossed in the occasional quote from St. Thomas Aquinas or the Greek reference from Greek classical literature. Though not an engineer, Barlow could decode complicated subject material like crypto policy, and boil down to what really mattered. Probably my favorite essay of this realm of Barlow, was the one that Mitch talked about it earlier. Crime and Puzzlement. It tells the story of the EFF, but so much more. Was written in 1990 and it runs just north of 10000 words. It begins with a showdown in cyberspace between Barlow and crackers and it goes on to a mediation of hacking ethics, an account of how the Sun Devil busts went down one, and of the first deep accounts of how civility goes to hell in online discussions. Of course the mythic origin of the EFF and the legendary visit of FBI agent Baxter to Barlow’s home in Wyoming. It’s a tour de force of storytelling. It’s a signpost of techno optimism and a warning against a threat to that promise.
As a matter of fact I urge you all to go to the EFF site and read it and the EFF does us all great favor by having an archive of Barlow’s work online. And I believe it’s ad free. [03:16:11]
Now I find it ironic that the Internet’s seemingly natural home as the font of creativity and free speech that Barlow so delighted on, is now under siege. The kind of complex long term expression that Barlow used to hack our minds with, is in danger of being overwhelmed and certainly outearned by 280 word bursts or a click baity post on Facebook. I have to admit though, that when I started to think about Barlow’s writing, I hadn’t realized how much he used those social media tools himself. Did you know that he had seventeen point five K tweets. That’s a lot there. But if you look at those tweets, it doesn’t have the virtuosity of the long form, and he’s talking to the audience that already loves him. And he also posts some photos of his last medical adventures of his later years, and I’m still trying to unsee those. [03:17:04]
So, I’ll stick to my views. There was tackling the harder stuff where Barlow made a difference. The harder stuff is really in danger of being marginalized or fatally underfunded today. Now as someone mentioned earlier, Barlow did finish a book. It’s actually going to be published in June. And in the first few pages, he describes when he finally decided to write his autobiography was when his heart stopped for eight full minutes. And that’s the quote I’m going to read from that. Let me read you that part. And here’s Barlow:
If people code out for 8 minutes like I did and then come back, they usually do so as a different person than the one who left. But I guess my brain doesn’t use all that much oxygen, because I appear to be the same guy. At least at least from the inside. For 8 minutes, however, I had not just been gratefully dead. I had been plain flat out ordinary dead. It was then I decided the time had come for me to begin working on my book. Looking for a ghostwriter was not really the issue. At the time my main concern was not to be a ghost, before the book itself was done.
So I suspect it wasn’t Barlow’s illness that led him to using a co-author, more like was a good idea to finally have someone who was going to get this book to a finish line. [03:18:15]
So the book is called “Mother American Night,” but I think of it, because I really got to advance copy and read it. Yes. Everything you know about Barlow was right. I don’t know how the division of labor worked out. I do feel it could have used the fact checker. My house in Massachusetts somehow transmogrified into to a farm in Vermont in this book. But the good news is first Barlow did get to the finish line and he actually wrote about its availability, shortly before he became a ghost, and he did it did it in a Facebook post. And a second piece of good news. Is this is authentically Barlow. Really in his voice. A voice which contains multitudes. It’s the story of what Zelig would have been, if Zelig had been an extrovert. So reading that book makes reading up book makes me think of how much we’re going to miss Barlow’s voice in this scary time for tech when our consensual hallucination is looking more and more like a bad trip. But that’s a different story. Thank you. [03:19:15]
Cory Doctorow: And now it falls to me to introduce my friend Joi Ito over there. And Joi is going to talk about community and you’ve heard today about Barlow and his relations to other people. You heard about how you could talk to him for ten seconds and you’d feel like he was your best friend. How he saw the good in all people. How he sought out people with alternate viewpoints to get their point of view and kind of to see where are the other people were coming from. I think that actually what was going on and all of those cases is partly just flat out liked people. He just flat out enjoyed hanging out with people and gabbing with them and gathering with them in odd places at all times and every time I met Barlow. I was just thinking this through. All the times I’d met Barlow, we’d arranged to meet somewhere. We’d be in Barcelona speaking at a conference and he’d ring me up and say, or email me and say, I’m not going to be at the conference party tonight. I’m going to an island, and you need to be at the island. And inevitably it would be three hours after my bedtime. And then he would show up two hours late to the island or to some odd nightclub in Montreal or a communal living situation on a mysterious boat in Mendocino. And wherever I met him. It was the middle of the night. He was surrounded by people working the room in a way that really can be described as anything less than virtuosic and having these conversations with people who are accomplished experts and tyros and pretenders and trolls and amazing people and dumb people and funny people. [03:20:50]
And the next thing you know, you have stayed up six or seven hours past your bedtime, had these incredible conversations, and you realise that Barlow just took the Internet around with them wherever he went. That it didn’t matter whether he was online or offline he was having the same experience wherever he was. And the last conversation I had with Barlow, he was in the hospital. And he said “you know when I get better I’m going to drive an Uber.” I’m like “you’re going to drive Uber?” “Yeah. I’m gonna drive an Uber. I’m just going to pick people up and I’m going to go you know what I’m John Perry Barlow. I wrote lyrics for the the Grateful Dead I helped found EFF, if you must have heard of them. You’re in San Francisco. Let’s just talk.’ and I’d just drive them around and we’d talk. We wouldn’t need to get there. They would give me five stars. I’m fine. I don’t need the money. But wouldn’t that be a trip.” [03:21:37]
So I say all this by way of introducing Joi Ito, because if there’s anyone else in the world who wants you to meet him three hours after bedtime in a place that isn’t the sanctioned conference event, it’s Joi. The person who managed to parlay dropping out of university into becoming the director of one of the most prestigious university institutions in the world by dint of many things, many virtues, but one of them is his absolute delight in having people just show up and talk to him with enthusiasm about the things that they are doing and giving them these sort of insightful bits of feedback and connections to other people and it’s a very Barlovian mode of conducting yourself. I’ve been around the media lab post and pre-Joi and Joi Media Lab is an extraordinary thing and it’s a thing whose linear roots you can trace back to those early days when the Internet was really just another kind of party that you conducted by other means. [03:22:37]
Joi Ito: Thank you Cory. I think my affliction is I’m easily influenced by amazing people and Barlow was one of them. You’re one of them. Were all – everyone here. I met Barlow and I know the date for that time because my mother had moved to L.A. and we were installing my sister in university in the summer of 1990 and Timothy Leary, who was amazing. He picked us up at the airport in L.A. Drove us to San Francisco. Said we’re going to have a party at the Mondo 2000 house. Who remembers Mondo 2000? (Everybody raises their hands.) OK. And we’re going to invite everybody. So first he did a party in L.A. And then they were going to invite everybody in San Francisco and included Barlow and then Barlow started dragging me around introducing me to everybody. And these two people – I’m like “California’s really amazing. Everyone’s so friendly and generous with their contacts.
Having Barlow and Timothy in the same room was like this very weird psychedelic sort of yin yang. Half of it overlaps. Half of it’s pushing against each other. But they had a lot of things in common, even though they had a lot of things that were opposite. and then. I’m gonna back up for a second cause this will tie into the story. Remembere the Mondo days for second. So the 90s. So there was this hippie bang right. So there was Barlow. There was Timothy Leary. There were a lot of psychedelics. This was when cyberpunk. Cause we didn’t have the internet really going yet it was like CD-ROMs and cyberpunk and drugs and leather and as I could see it was a fashion movement and we were all pretty excited about the future. it’s VR. Remember we had Toontown that had free VR and VR was a thing. And tripping and doing VR and remember when South Park was like a needle park. And it was before wired took it over and sort of gentrified it. And so that was actually really important. [03:24:40]
And then Silicon Graphics was coming and then Silicon Graphics became the rave flier computer that made the design for Wired. And so there was a culture back then when Silicon Valley actually was part of this extended hippie movement. And it was before all of this Silicon Valley thing going on right now. And so… but a lot of us here when I look around and listening to John that thread that comes from the hippie movement which is a kind of weird sense of optimism. It’s a sense of humor. But it’s a sense of humor and optimism that’s very different than the giddy optimism of an investor during a bubble. This is this is the optimism that you see and the sense of humor that you see when you talk to the Dalai Lama.
I got lucky that (…) introduced me. Hunter Thompson carried around the lawyer. I travel with a monk. But anyway, when you talk to the Dalai Lama. Just like when you talk to John Perry Barlow, there’s a deep sense of humor that comes from knowing how fucked up the world is. How unjust the world is. How terrible it is. But still being so connected to nature that it’s so funny. This is that thing you’re talking about. (Looking at John Gilmore.) You can get it through a mind expanding drugs. You can get it through meditation. Somehow the greatest people I know, somehow stumble there and I think that was…
Tim had that in his own way. And Barlow had that. And one of the things that Tim often said was “question authority and think for yourself.” And I live by that and this just relates a lot to a lot of what John, you were saying. And so, Barlow and I would talk about this and I also took a detour to Pinedale, not on my private jet, and as my doppelganger said that’s another story. [03:26:28]
And I tried to write a book with him and it failed and that’s another story. But one of the things that for me was really important was the Declaration of Independence for Cyberspace. That was like a battle cry for us to rally around and it took this kind of fashion movement of the cyberpunks and turned it into a political social movement that tied a bunch of things together. But today we look around and it seems like kind of a distant dream. And I’ll read something that Barlow said was “My belief in the virtues of giving all humanity a voice, did not take into account what would happen if you gave everyone a billion people their own virtual soapbox on a street corner. And I still remember in the early days when we thought “we just connect everybody together and we’d have world peace” ya know, and the Internet would just solve everything. And that technology can be political. We can design it in a way that the bad guys couldn’t use it. Well turns out, it’s wrong. But I think he was aware. He was aware of this winding path and I think the manifesto was a compass heading. This is where we’re going. And just like any compass heading — do you guys know the story of a Donner Party – (Everybody shakes their head YES!) It feels like the winter of 1846, when were in the mountains of Sierra no food resorting to cannibalism, but someday we will get to California and that’s where we’re headed. And so I feel like we’re kind of in this dark moment. But Barlow also says “I’m not sorry I wrote it. One day. I still believe it will seem true.” And I think what’s really important is that we still look at this as a compass heading and that we don’t look at these dark moments of today as the end. It’s a path that we’re taking on the way. [03:28:13]
I also believe that someday will be true, but it doesn’t happen just by waiting. It requires – and this is another thing that Barlow did – he set the compass heading. But he also organized. He created tenacity and he fueled all of us to get shit done, even though he was late a lot, to build these organizations. To go out and be active. And the activism that you get from this optimism and his passion and his humor is a very different kind of activism than that which is fueled purely by hate, and I think this is actually an important part of what he was. And so it’s – I think we’re in a very dark moment. I think we’re in the darkest moment that I can remember. I was born in 1966. It turns out 1967 was kind of a weird year. It was the year the Detroit – we call them riots. Some people call them “rebellions.” I think we call it they’re called riots because they weren’t successful in the rebellion. But I mean 43 people were killed. Fourteen hundred buildings were burned. The National Guard were called out. I mean this is a pretty dark moment. But it’s also the year that the Grateful Dead album debuts it’s the year that Barlow takes the dead to Millbrook to meet Timothy Leary. It’s also the year of the Summer of Love which kicks off the hippie movement. And if you think about and remember if you were older than me or read or watch the archives. The hippies fought against these racial tensions; against the Vietnam War. Not with anger and violence but they fought it with songs and love. And this cultural movement and I think in a kind of kindness, right?. [03:29:54]
And I think that’s actually pretty important because today I feel like with the parkland kids with #metoo and #timesup. I mean #metoo in terms of, this questioning you know centuries of patriarchal power. And there’s a lot of power in this. But one thing I think that we need to remember — and they’re coming I think to try to overthrow this establishment that you’ve been talking about. And they’re coming to burn down the building. This is a real, I feel rebellion, and revolution in the air. And so as I start to think about this and look at it. They’re are still somewhat serious. You know and I think that we have this. It’s different from the hippie movement but I think what we have to remember is and I hear Barlow’s laugh in my head when I think about this. But he had such an elegant way bringing together the humility the humor the optimism together with that hard hitting and activism and resolve. And I think that we need to make sure that this tidal wave of activity that’s coming has that sensibility. And I think that this community has that is I can hear from all of people’s presentations and and then somehow I think we need to instill and bring back maybe through using psychedelics. But I do think that we can fiddling with the rules is one thing but the power structures are only going to change in a lasting way if we change the paradigms that feed them, and you change the paradigms that feed them through cultural change, not by merely winning the argument. So I will end. [03:31:33]
I’ll end with actually the last paragraph, a few sentences, of the manifesto. Because I think they’re actually relevant; that’s the compass, Barlos said “we will create a civilization of the mind in cyberspace. May it be more humane and fair than the world your governments have made before. And I think that’s our compass heading.
Cindy Cohn: Thank you. If folks have questions I think the offers are still here to come through the files and pick them up. I have quite a few from the last round as well. So but we’ll have watch for the EFFers in their hoodies and elsewhere to pick up the things. Raise them up high, so people can see them. Here’s a question probably for Gilmore. This year marks the 20th anniversary of EFF’s work on the DES cracker. How would Barlow view the state of encryption and its impacts today? [03:32:37]
John Gilmore: Let’s see. The DES cracker actually had its desired effect which was to push the rest of the world to stop relying on an insecure cipher. And we’ve been pretty successful at pushing at least part of the world that uses the Internet to use much more secure communications. The EFF’s efforts to secure Web sites and to make that process easy has made a dramatic improvement in the fraction of communication that goes over the Internet that is encrypted.
On the other hand, back in the 90s we kind of decided we won the crypto wars and what we won was the legal right to deploy encryption. But what we failed to win was actually deploying it everywhere it was needed, and in particular on cell phones. So cell phones of course have become surveillance devices, and they are now one of the threats to privacy and threats to autonomy and one of the props of centralized control. So I’d say it’s kind of, you know, a mixed record. [03:34:49]
Cindy Cohn: Thanks. Maybe for Shari or any of you actually. Looking to the future (garbled question) So I believe if I can rephrase this “looking to the future how can freedom of the press or freedom of the Internet be manipulated by would be tyrants and how do we fight it?” I added that last part myself.
Shari Steele: Is that a hypothetical? I’m having little bit of trouble with this because I think we are seeing how it can be manipulated by would be tyrants, and that’s it’s pretty terrifying actually, because it requires us to be diligent about about paying attention and about following trails and about being honest with what actually is happening. The people who have the knowledge sharing that with us. I don’t know how that’s going to play out. I know that right now it makes it very scary. It brings a darkness to the communications that are not not making me feel comfortable.
Cindy Cohn: How do we inspire a new generation of Barlows? Well it’s a little… isn’t it a little like the Dalai Lama right? When there are the monks when they die and the other one will be born. Right. So that’s my view. We should figure out yeah maybe we can get some some of our friends here on that. Yeah well we do we’ve got his granddaughter here!
Cory Doctorow: I think more seriously, Barlow inspired a generationof Barlows. You just heard Snowden Snowden talk about how he did it possibly the most politically disruptive thing in modern American history because he read some words Barlow wrote and followed the example that Barlow set. That he was morally persuaded by the things that Barlow wrote. So, I think if you want to inspire another generation of Barlow on the one hand you can spread Barlows writings. But on the other hand you could have those conversations with the people around you about why this stuff matters to you. I know it sucks to be the person from Amway who always just wants to talk about how great Amway is but it’s an important conversation and this is the moment to be having it. [03:36:58]
Cindy Cohn: OK here’s an easy one. Or a fun one anyway. What was the strangest place you ever unexpectedly bumped into Barlow.
Steven Levy: You know there could be no place so strange that you wouldn’t expect Barlow, because he could be anywhere. Yeah but it was always amazing the number of times you would talk to someone. And it turns out that they too were Barlow’s best friend. Well, I did see him once at the beginning of an EFF Board meeting, and the way this happened was he was living in my house. And it always took him several hours to get ready. He was, his mobility was challenged. He had 24 hour helpers helping him get dressed and eat and all that stuff. And he talked about us going down to the board meeting together and I said “Barlow I can’t do that.” And he said “why not?” I said “because I’m going to be there on time.” And that pissed him off and he actually made it for once. [03:38:23]
Cindy Cohn: John another quick one for you, which is “When did you meet Barlow and how?
John Gilmore: Ah well of course I met Barlow in cyberspace. The Exploratorium here in town has a thing called the Tactile Gallery which we used to call the “Tactile Dome” and it’s a place it’s dark inside where you can crawl around and you bring a whole bunch of people through, and because you can’t see, you’re forced to feel everything around you. And they’ve put in all of these different textures designed for you to feel. So it’s just an exploration of that sense. Well it used to be that if you were an Exploratorium member, you could book the tactical dome. I think you still can for an evening adventure. And if everyone in the party wanted to go through naked they could for the full tactile experience. [03:29:27]
And so, I was organizing a group like this, and you know clearly if you want to do this you don’t invite anybody who doesn’t want to go naked. And so, I put this out to my group of friends, and I had a list of 25 people or however it would hold. And somebody somehow the word got around on the well that this was happening and Barlow was like “I want to try this.” And so he sent me an email, and said you know is there room in this thing and I said well no it’s all booked up. But my experience is usually on the day it happens a couple of people don’t show up for one reason or another. So if you do show up you’ll probably get in. And indeed he showed up at the Palace of Fine Arts, which is where the Exploratorium was back then, and came in his cowboy hat and his armadillo boots. And he got in and crawled around naked in the dark with us for a couple hours. [03:40:38]
Cindy Cohn: Times have changed. Probably not. For John.
John Gilmore: And I think they make you wear underwear.
Cindy Cohn: So we’ll go back to a more serious one, but I’m really glad we got that story out. What are the solutions to deal – this might be good one for Joi. What are the solutions to deal with machine big data messaging that are not honest expressions but intended to coerce control and even limit people’s thoughts and speech? How vulnerable is human thought and decision making to at scale computational propaganda.
Joi Ito: Ok so. I’m going to say this in a somewhat compact way. So I do think that we overestimate a little bit, the Cambridge Analytical stuff. Just for what it’s worth. I think there’s a lot of sales talk, but it’s pretty hard to change people’s political opinions. It’s a big deal. And as Cory said, :this is a crisis we can’t afford to waste.” [03:41:46]
But I think more broadly I would say that this sort of obsession. First of all, with just controlling your data. That’s important. But what we really need to do is to have input, public input, and the way we do that is really important. To the design of the algorithms as well as what they’re being optimized for, and right now that process. And this is a longer conversation and it ties to something that Mitch was saying, is that the government as an information in fiduciaries; EFF and ACLU. But we don’t really have a very good way of managing this process, because the government, which is usually with people who do it, is kind of dysfunctional. So, I do think that we talk about data privacy. We talk about a lot of things but we need the engineers and the social scientists and lawyers to come together to create a system that is… The technology has to be designed in a complete different way. [03:42:41]
We’re trying to do it by getting the engineers to understand social scientists and getting the lawyers and social scientists understand engineering, because it’s actually a design problem of the whole system, so it’s not an easy fix. You can’t just – you have to pass laws but you can’t just pass laws. You have to change code, but you can’t just change code.
So this is where at MIT it’s really – I’m really sort of in the middle of this, which is, you have to train people who understand all of this, and this is where Barlow will fit into this, is he could talk to all these people. We need the translators, who not only translate the literal things. You have to translate the intent. The values. And my point about changing the paradigms, which is I think the most important thing, which is you know: greed is good. The more shit you have the happier you are. All of these sort of neo liberal you know financial measurement of success of things are also the paradigm that feeds what we’re optimizing for.
And that actually requires I think a cultural intervention by Cory’s book Walkaway. I mean we need to get everybody to just say “Fuck this shit! I will not have those values.” And fundamentally you can tinker with the code and you can tinker with the laws. But unless the paradigm changes, the goals don’t change. Unless the goals change… So I’m going to go one last thing…[03:43:59]
Everyone knows a monopoly. So there’s a game that is the predecessor to monopoly called “the landlord’s game,” which is a 1904 game by the Georgia’s to show it was a game show the perils of rent and the perils of capitalism to teach kids how horrible capitalism was. Parker Brothers takes the game. Doesn’t change the rules. They change the goal. Now the captain was trying to make your best friends bankrupt. And so my point here is that it’s the goal, not the rules. So having said that, it’s important for EFF and everybody work on the goals. But the really important thing – this is where Barlow was gunning for it – is you have to change the values and the values change the paradigms and that requires poetry and music and so that’s actually at the end I think, the way we’re going to deal with all these problems. [03:44:45]
Cindy Cohn: Here’s another one that I’m not sure who will be best for this, but I may go back to Joi or Steve. With the advent of artificial intelligence, what are the opportunities to progress Internet freedom and what are the dangers presented? Should we be worried?
Steven Levy: Yeah. Well, of course we should be wary, but it isn’t just the AI. It is, you know, what Joi is saying, is the larger construct of things. How these things are going to be used. What we hear a lot is AI is going to help us. It’s going to identify the wrongdoers and fix that. But again the which is what you’re optimizing towards, and who’s doing it, is what is going to be helpful there. The optimist in me thinks that things will balance out towards what people need. Right? So we’ve been talking about free speech and you know, where we are in terms of people manipulating what we think. And I think we’re already kind of getting the end of that swing of the pendulum there, where people are going to be less tolerant to it. And there’s going to be a movement to curb that and change that . So I’m betting that the pendulum will now start moving towards a way where it isn’t so destructive. (Optimistic.)
Cindy Cohn: Here’s one maybe for Shari. Some people are advocating for an Internet Bill of Rights or a digital bill of rights. Net neutrality is now controversial (Cindy looks up and says “not in my house.”) How can we be sure that government regulation is appropriate for something like the Internet which is supposed to protect free thought. I did. I took some liberties with that question. [03:46:55]
Shari Steele: It’s a really hard one. So government regulation is a double edged sword. And anytime that we are trying to bring the government in you have to make sure that there isn’t overreaching. And a piece of legislation, as it gets started, as it was originally introduced often gets compromised in ways that you sometimes can’t even imagine what’s going to happen to it. That’s all a very long winded way of saying that it would be very difficult for me to answer that question in a vacuum. A particular piece of legislation is really the way you need to look at these kinds of issues as to whether or not it could be the solution that you’re looking for. I’m not doing day to day long legal work anymore, so I think that there are probably better people including Cindy, to answer this question so maybe she has something more enlightened than what I just shared. [03:48:04]
Cindy Cohn: Sure. I think that a way to parlay that. See what she does. I do think that the questions we need to ask ourselves is not whether the government should pass laws that regulate the Internet or whether it shouldn’t. I think there were some fundamental questions about that maybe early on, but the internet has always been a place where a law was going to apply in one way or another, and we have to ask ourselves the harder questions which is “How do we want law to apply in the online environment? And how do we make sure that we protect freedom from law even in this space where there’s going to be laws.” So Shari’s right. We do look at each question individually. I’ve never been sure that we needed an Internet Bill of Rights because we have a Bill of Rights. I’ve never thought that we needed Universal Declaration of Internet Rghts because we have an International Declaration of Human Rights and until we have the AI and we have to figure out what that codicil looks like. I think those rights will hold for us. If we’re smart, and we’re thoughtful, and we think carefully about how we want to apply them in this new context. I don’t think people need to worry. I don’t think we want to start from scratch again about whether we think the right for freedom of expression is something we want to protect or whether we think people want to be protected against search and seizure or whether we think people want to be able to be protected against summary execution. I think humanity’s thought all that through already and we came to mostly the right decisions. We need to make sure that we’re hyper careful about how those things get presented in in this new environment. And frankly that’s been my worry for the last 28 years and I don’t think we’re done yet. [03:49:58]
Cory Doctorow: I was just going to propose that some of our colleagues at the Free Software movement came up with some pretty good principles for kind of setting the contours of what might make a good rule or what we should look out for in making a bad rule, which is that in order to know whether or not our computers are serving us, we need to be able to examine how they work. We need to be able to communicate to other people what we discover about them and we need to be able to change how they work if they don’t suit us. And so I think that if you look at EFF’s work over the last 25 years, you see so many of the fights that we are in are about one or more of those principles. And really if we start with those as first principles I think we end up with a lot less mischief in our law.
Cindy Cohn: So I have one one little surprise guest. Bob Hilleman would you come up please. We were sent some greetings by someone and Bob has kindly offered to present them to us. [03:50:57]
Bob Hilleman: Hello. Just briefly driving down today and I has a chance to talk in the car with Dan Ellsberg, who today turned 87. It’s his birthday today, and and he’s back in Washington D.C.. A tireless warrior, at 87, and he’s really wishing he could be here with each and every one of you. Because he just feels like this is his tribe too, and he wants to be here. But he’s busy today in Washington. And I just want to say if you haven’t been aware of the fact that his latest book, which he just finished writing, The Doomsday Machine; He considers it more important than the Pentagon Papers, and certainly as important as anything he’s ever done. And so – and this is in part what I want to say – is you’re never too old to keep doing something important. We’ve all been at this for a long time and we’re not done yet. None of us are done yet. So that’s important to hold onto when you’re 87 you do your best work. What can you say? Anyway. Hello from Dan.
Cindy Cohn: I want to thank the panel. We’ll let you go. If you guys want to get a go, you can or you can stay here. Next up I’d like to buy Amelia Barlow who has some words for us as well. [03:52:32]
Amelia Barlow: I want to just say I have the easiest job in this room. I would say. Because all I have to really do up here is say thank you, to all of you. I want to say thank you for embodying these ideas that were shared today. Continuing his legacy in the way that you work in the way that you live your lives. Also thank you for being the immune system, and protecting us from tyranny.
When he passed he entrusted us with the most valuable asset that I could possibly imagine, which is you. All of the people in this room. All of the people around the world who he cared about and cared about him.
This vast web of infinitely interesting and radical human beings that he gave to us. And I really appreciate that. So one of his guiding beliefs that I found really interesting is like the conservation of energy and this principle. No idea was created or destroyed. As you’ve heard many times today. So in that – all these all of this creativity is pulled from and return to this sort of cosmic soup or the Noosphere as Alden told me. This endless creative force has to be drawn upon anywhere at any time by anyone. As he shuffled off his meat prison. It seemed to be at the end there. He told me I was his squishy ware. There was almost an eruption of creative force. This sequestered essence that was living inside of him and he was immediately returned to this this collective soup pot. I feel like as he’s passed he’s almost bigger and bossier and more ubiquitous than ever. Certainly my life has been taken over.
But I just I feel like, in closing to this beautiful symposium. I just want to say that never before have you been able to draw more immediately and completely upon him. And I want you to feel that. So if you would do me – indulge me I guess I should say. And I want everybody to stand up. Please. [03:55:26]
I want you to stand up and close your eyes. I want you to take a moment. And really drink him. I want you to feel his essence. His thoughts. In this room. Feel him in the person next to you. I want you to feel him in the glorious light streaming through these windows. Feel him in the love in your heart. Feel him in the magic of opening yourself to this creative force. In this raw spirit. This unbridled freedom that he now has attained. [03:56:20]
1) Be patient. No matter what.
2) Don’t bad mouth. Assign responsibility. Never blame. Say nothing behind any other’s back that to you’d be unwilling to say in exactly the same tone and language to his face.
3) Assume the motives of others are never to them, less noble, than yours are to you.
4) Expand your sense of the possible.
5) Don’t trouble yourself with matters you truly cannot change.
6) Expect no more of anyone than you yourself can deliver.
7) Tolerate ambiguity.
8) Laugh at yourself frequently.
9) Concern yourself with what is right rather than who is right.
10) Never forget. No matter how certain; you might be wrong.
11) Give up bloodsports.
12) Remember your life belongs to others as well. Do not endanger it frivolously and never endanger the life of another.
13) Never lie to anyone for any reason. Lies of omission are sometimes exempt.
14) Learn the needs of those around you and respect them.
15) Avoid the pursuit of happiness. Seek to define your own mission and pursue that.
16) Reduce your use of the first personal pronoun.
17) Praise at least as often as you disparage.
18) Never let your errors pass without omission.
19) Become less suspicious of joy.
20) Understand humility.
21) Forgive.
22) Foster dignity.
23) Live memorably.
24) Love yourself.
25) Endure.
26) Don’t be a dick.
Thank you.
Cindy Cohn: OK. That was beautiful. Thank you Amelia. (Hugs) [03:59:12]
Following that is not going to be easy. I just really felt him in the room. Didn’t you all? It was amazing. But I want to point us forward, and I wouldn’t be the Executive Director of the EFF if I didn’t point us forward towards some fights, and some things that we’re going to need to do.
One of my favorite ideas, came from Barlow, during one of my earliest meetings at the EFF as a legal director, when we talk about how are we going to make sure that people kept their rights as we moved into cyberspace and he encapsulated in an essay that’s called To Be At Liberty:
“Whatever the guarantees I believe liberty resides in its exercise. Liberty is really about the ability to feel free and behave accordingly. You are only as free as you act. Free people must be willing to speak up and listen. They can’t merely consume the fruits of freedom, they have to produce them. This exercise of liberty requires that people trust one another and the institutions that they make together. They have to feel at home in their society. [04:00:40]
Imagine a world quite soon to come in which ideas can spread like fire. As Jefferson said: “expansible over all space without lessening their density at any point. And like the air in which we breathe, incapable of confinement or exclusive appropriation by anyone. If ideas can spread like fire then freedom, like water, will flow around or over those who stand in its way.
In cyberspace, I hope this truth will be self-evident.”
Cindy Cohn: I think it hasn’t turned out that way, at least not yet. And in some ways it does feel like we’re in a time that is much darker and much murkier. But I think that his hopes and dreams were the right ones. And now, without him, it is up to us to make them come true. [04:01:38]
Finally, he said, “Liberty has its downsides, though considering the alternative, I’ll cast my lot with freedom.”
Cory Doctorow: I’m gonna read a Barlow quote too:
“Most libertarians are worried about government but not worried about business. I think we need to be worrying about business in exactly the way we are worrying about government.”
Cory Doctorow: So, we’re living in a public/private partnership from hell right now, and the only way it’s cost effective to spy on everyone on Earth, plus or minus some statistical rounding error, is because we foot the bill for it by paying for services and voluntarily using them in ways that surveil us. And if you think that governments are going to rein in the surveillance that they depend on from the private sector, you’re not paying attention.
So we need to fight not governments, not companies, but the zealous exercise of coercive power over us. And if there’s a Barlovian sentiment, I think that’s it. There are important struggles on our horizon that dwarf the fight over the destiny of the Internet: The destiny of our planet and its climate, the destiny of our economic relationships and our inequality, the destiny of the relations between people of different backgrounds, genders and gender expressions – all infinitely more important than the fight over the destiny of the Internet, but not more foundational. [04:03:10]
Because the Internet is not a recruiting system for jihadis, and it’s not a video on demand service, and it’s not the world’s greatest pornography distribution system. It’s the nervous system of the 21st century and it’s the terrain on which all of our future fights will be fought.
And there is a great risk as we set out to solve these enormous problems about the future of our global nervous system that we will arrive at the security syllogism. That favorite tool of everyone faced with some kind of crisis that seems intractable. It goes like this. Something must be done. There, I’ve done something. We need meaningful real hard solutions to meaningful real hard problems about how we make an Internet that enhances human freedom, instead of taking it away. And there is a real problem in the way that powerful institutions view those of us who make them up, to those of us who are under them, they view us as their inconvenient gut flora. And they view – the institutions themselves – take on the character of a kind of immortal colony organism from which we can be jettisoned, if we prove to be inconvenient. [04:04:16]
But there is an enormous difference between your actual gut flora – which can and at times get you in enormous trouble – and the human beings who labor, in the surveillance apparatus, who labor in companies. Who are our friends and our loved ones, our neighbors here in this city. And that is that human beings are subject to moral suasion and you can’t win an argument with bacteria. And one thing that Barlow taught us is that writing words and having arguments and talking to people changes the world.
I was once privileged to be part of a group of people who draftedsomething called the Access to Knowledge treaty — whose latest embodiment is the Marrakesh Treaty – and we started in an office at 7 in the morning on a Sunday in Geneva at the Médecins Sans Frontières offices with, the instigator to that – a guy named Jamie Love. And someone said to Jamie. “How do you think that we’re going to make a single bit of difference, here in this city, in this world, with this ambitious idea of extending universal access to all human knowledge?” And he said “You know, the WTO was founded in a room not far from here by people no smarter than you, who had ideas that were no better than yours, and they went on to change the entire world. In fact everything that ever happened in this world to make a change started with people no different than you. No smarter than you. No better connected than you. No more persuasive than you. Who had an idea and worked together to make it happen. And if terrible ideas can happen that way, then so can good ones.” [04:05:44]
So, I’m going to ask you today to walk away from this and do something Barlovian. I want you to go have a talk. Because if you live here in this city you know tons of people who are primed to understand the importance of the Internet and keeping it secure. And you may think that it should be self-evident that working on missions like those of the Freedom of the Press Foundation and the Electronic Frontier Foundation and all of our other fellow travelers that that is the most important thing they could do to safeguard this future that they’re so heavily engaged in building. But I can tell you that the numbers of subscribers to Hacker News or readers of the technical forums on Reddit or even the subscribers of Slashdot dwarf the membership rolls of all of our organizations. There is so much low hanging fruit for you to go out and pick this week. Sit down and have a conversation with someone who’s already primed to understand the importance of technology and its relationship to human flourishing and liberty. And that I want you to go varsity and I want you to have that conversation with someone non-technical. Someone who doesn’t understand how technology could be a force for good but is maybe becoming keenly aware of how technology can be a force for wickedness. And ensure that they are guarded against the security syllogism and sure that they understand too, that we need not just to understand that technology can give us problems, but we must work for ways in which technology can solve our problems too.
And if you do those things you will honor the spirit of John Perry Barlow in a profound way that will carry on from this room and honor our friend, who we lost so early, and who did so much for us. Thank you. [04:07:28]
Cindy Cohn: So, you have your marching orders. You’ve been inspired. We got to have a moment to have what Wavy Gravy calls some good grief together. So go on. You’ve got work to do. We all do. I want to thank the Internet Archive for moving heaven and earth to make sure that we can have this day together today. I want to thank the EFFers who helped make this whole thing happen. I especially want to call out Aaron Jue our development director and Lindsey Oliver who dropped everything to make this happen.
I want to thank again, the Barlow family for being so gracious and letting us celebrate their loved one and letting us have him, so that we could all love him too. He left us with a lot of work to do but he gave us a north star. So let’s get at it. Thank you.
Complete Transcript – Transcription by Lisa Rein (Co-founder Aaron Swartz Day & Creative Commons, and friend of John Perry Barlow). Lisa Rein used Teme to start – and then cleaned it up by comparing it to the video, over many days :)